Greater than 600,000 small workplace/house workplace (SOHO) routers are estimated to have been bricked and brought offline following a damaging cyber assault staged by unidentified cyber actors, disrupting customers’ entry to the web.
The mysterious occasion, which occurred between October 25 and 27, 2023, and impacted a single web service supplier (ISP) within the U.S., has been codenamed Pumpkin Eclipse by the Lumen Applied sciences Black Lotus Labs group. It particularly affected three router fashions issued by the ISP: ActionTec T3200, ActionTec T3260, and Sagemcom.
“The incident occurred over a 72-hour interval between October 25-27, rendered the contaminated gadgets completely inoperable, and required a hardware-based substitute,” the corporate stated in a technical report.
The blackout is important, not least as a result of it led to the abrupt elimination of 49% of all modems from the impacted ISP’s autonomous system quantity (ASN) in the course of the time frame.
Whereas the identify of the ISP was not disclosed, proof factors to it being Windstream, which suffered an outage across the identical time, inflicting customers to report a “regular purple mild” being displayed by the impacted modems.
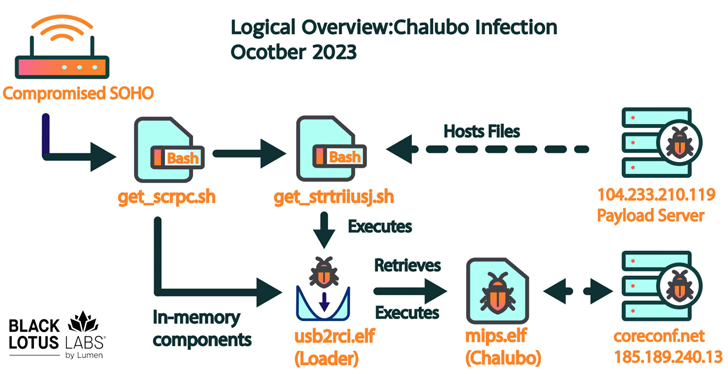
Now, months later, Lumen’s evaluation has revealed a commodity distant entry trojan (RAT) known as Chalubo – a stealthy malware first documented by Sophos in October 2018 – as chargeable for the sabotage, with the adversary choosing it presumably in an effort to complicate attribution efforts moderately than use a customized toolkit.
“Chalubo has payloads designed for all main SOHO/IoT kernels, pre-built performance to carry out DDoS assaults, and might execute any Lua script despatched to the bot,” the corporate stated. “We suspect the Lua performance was doubtless employed by the malicious actor to retrieve the damaging payload.”
That stated, the precise preliminary entry technique used to breach the routers is at present unclear, though it is theorized that it could have concerned the abuse of weak credentials or exploited an uncovered administrative interface.
Upon gaining a profitable foothold, the an infection chain proceeds to drop shell scripts that pave the best way for a loader in the end designed to retrieve and launch Chalubo from an exterior server. The damaging Lua script module fetched by the trojan is unknown.
A notable side of the marketing campaign is its concentrating on of a single ASN, versus others which have usually focused a particular router mannequin or frequent vulnerability, elevating the likelihood that it was intentionally focused, though the motivations behind it are undetermined as but.
“The occasion was unprecedented because of the variety of items affected – no assault that we are able to recall has required the substitute of over 600,000 gadgets,” Lumen stated. “As well as, one of these assault has solely ever occurred as soon as earlier than, with AcidRain used as a precursor to an energetic navy invasion.”