The homepage of Stark Industries Options.
Two weeks earlier than Russia invaded Ukraine in February 2022, a big, mysterious new Web internet hosting agency known as Stark Industries Options materialized and shortly grew to become the epicenter of large distributed denial-of-service (DDoS) assaults on authorities and business targets in Ukraine and Europe. An investigation into Stark Industries reveals it’s getting used as a worldwide proxy community that conceals the true supply of cyberattacks and disinformation campaigns in opposition to enemies of Russia.
No less than a dozen patriotic Russian hacking teams have been launching DDoS assaults because the begin of the struggle at a wide range of targets seen versus Moscow. However by all accounts, few assaults from these gangs have come near the quantity of firepower wielded by a pro-Russia group calling itself “NoName057(16).”
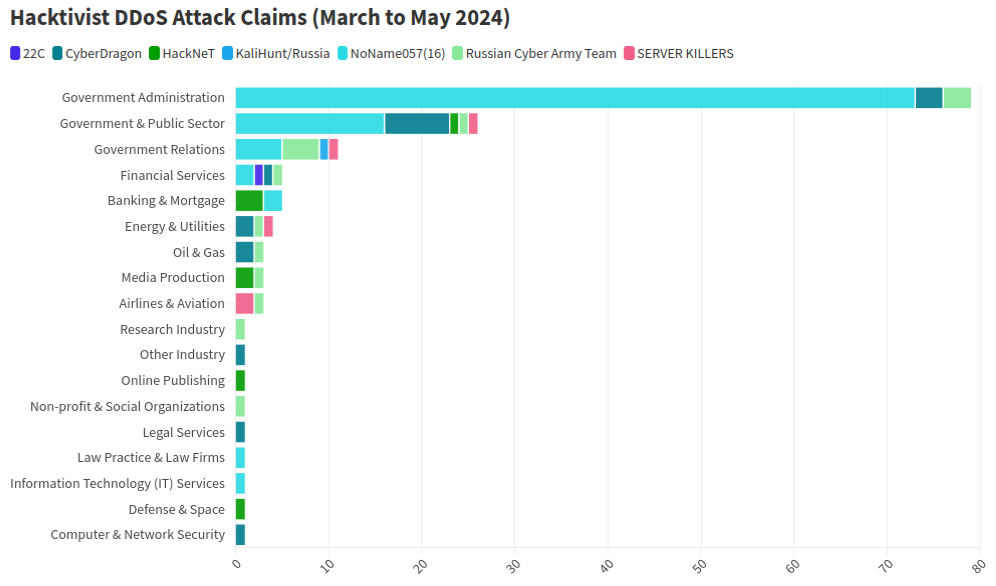
This graphic comes from a current report from NETSCOUT about DDoS assaults from Russian hacktivist teams.
As detailed by researchers at Radware, NoName has successfully gamified DDoS assaults, recruiting hacktivists by way of its Telegram channel and providing to pay individuals who agree to put in a chunk of software program known as DDoSia. That program permits NoName to commandeer the host computer systems and their Web connections in coordinated DDoS campaigns, and DDoSia customers with probably the most assaults can win money prizes.
The NoName DDoS group promoting on Telegram. Picture: SentinelOne.com.
A report from the safety agency Staff Cymru discovered the DDoS assault infrastructure utilized in NoName campaigns is assigned to 2 interlinked internet hosting suppliers: MIRhosting and Stark Industries. MIRhosting is a internet hosting supplier based in The Netherlands in 2004. However Stark Industries Options Ltd was included on February 10, 2022, simply two weeks earlier than the Russian invasion of Ukraine.
PROXY WARS
Safety consultants say that not lengthy after the struggle began, Stark started internet hosting dozens of proxy companies and free digital non-public networking (VPN) companies, that are designed to assist customers protect their Web utilization and placement from prying eyes.
Proxy suppliers permit customers to route their Web and Internet searching site visitors by another person’s pc. From an internet site’s perspective, the site visitors from a proxy community consumer seems to originate from the rented IP deal with, not from the proxy service buyer.

These companies can be utilized in a legit method for a number of enterprise functions — corresponding to worth comparisons or gross sales intelligence — however they’re additionally massively abused for hiding cybercrime exercise as a result of they will make it tough to hint malicious site visitors to its authentic supply.
What’s extra, many proxy companies don’t disclose how they get hold of entry to the proxies they’re renting out, and in lots of circumstances the entry is obtained by the dissemination of malicious software program that turns the contaminated system right into a site visitors relay — normally unbeknownst to the legit proprietor of the Web connection. Different proxy companies will permit customers to generate profits by renting out their Web connection to anybody.
Spur.us is an organization that tracks VPNs and proxy companies worldwide. Spur finds that Stark Industries (AS44477) at present is dwelling to at the least 74 VPN companies, and 40 completely different proxy companies. As we’ll see within the remaining part of this story, simply a type of proxy networks has over one million Web addresses out there for hire throughout the globe.
Raymond Dijkxhoorn operates a internet hosting agency in The Netherlands known as Prolocation. He additionally co-runs SURBL, an anti-abuse service that flags domains and Web deal with ranges which can be strongly related to spam and cybercrime exercise, together with DDoS.
Dijkxhoorn mentioned final 12 months SURBL heard from a number of individuals who mentioned they operated VPN companies whose net assets had been included in SURBL’s block lists.
“We had individuals doing delistings at SURBL for domains that had been suspended by the registrars,” Dijkhoorn informed KrebsOnSecurity. “And at the least two of them defined that Stark provided them free VPN companies that they had been reselling.”
Dijkxhoorn added that Stark Industries additionally sponsored activist teams from Ukraine.
“How worthwhile would it not be for Russia to know the actual IPs from Ukraine’s tech warriors?” he noticed.
CLOUDY WITH A CHANCE OF BULLETS
Richard Hummel is risk intelligence lead at NETSCOUT. Hummel mentioned when he considers the worst of all of the internet hosting suppliers on the market as we speak, Stark Industries is persistently close to or on the high of that listing.
“The reason being we’ve had at the least a dozen service suppliers come to us saying, ‘There’s this community on the market inundating us with site visitors,’” Hummel mentioned. “And it wasn’t even DDoS assaults. [The systems] on Stark had been simply scanning these suppliers so quick it was crashing a few of their companies.”
Hummel mentioned NoName will usually launch their assaults utilizing a mixture of assets rented from main, legit cloud companies, and people from so-called “bulletproof” internet hosting suppliers like Stark. Bulletproof suppliers are so named once they earn or domesticate a fame for ignoring any abuse complaints or police studies about exercise on their networks.
Combining bulletproof suppliers with legit cloud internet hosting, Hummel mentioned, doubtless makes NoName’s DDoS campaigns extra resilient as a result of many community operators will hesitate to be too aggressive in blocking Web addresses related to the most important cloud companies.
“What we usually see here’s a distribution of cloud internet hosting suppliers and bulletproof internet hosting suppliers in DDoS assaults,” he mentioned. “They’re utilizing public cloud internet hosting suppliers as a result of numerous instances that’s your first layer of community protection, and since [many companies are wary of] over-blocking entry to legit cloud assets.”
However even when the cloud supplier detects abuse coming from the client, the supplier might be not going to close the client down instantly, Hummel mentioned.
“There’s normally a grace interval, and even when that’s solely an hour or two, you’ll be able to nonetheless launch a lot of assaults in that point,” he mentioned. “After which they only hold coming again and opening new cloud accounts.”
MERCENARIES TEAM
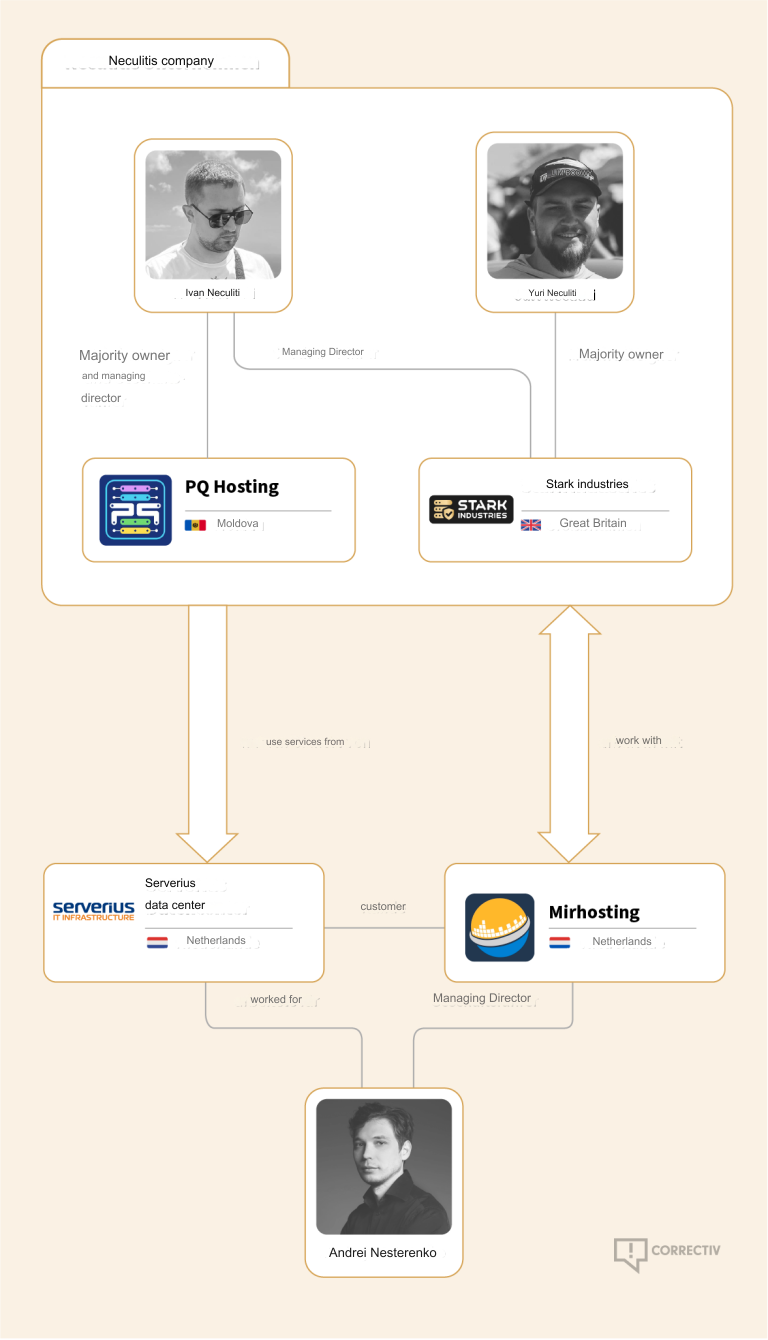
Stark Industries is included at a mail drop deal with in the UK. UK enterprise information listing an Ivan Vladimirovich Neculiti as the corporate’s secretary. Mr. Neculiti additionally is known as because the CEO and founding father of PQ Internet hosting Plus S.R.L. (aka Good High quality Internet hosting), a Moldovan firm shaped in 2019 that lists the identical UK mail drop deal with as Stark Industries.

Ivan Neculiti, as pictured on LinkedIn.
Reached by way of LinkedIn, Mr. Neculiti mentioned PQ Internet hosting established Stark Industries as a “white label” of its model in order that “resellers might distribute our companies utilizing our IP addresses and their shoppers wouldn’t have any affairs with PQ Internet hosting.”
“PQ Internet hosting is an organization with over 1,000+ of [our] personal bodily servers in 38 international locations and we’ve over 100,000 shoppers,” he mentioned. “Although we aren’t as massive as Hetzner, Amazon and OVH, however we’re a quick rising firm that gives companies to tens of 1000’s of personal clients and authorized entities.”
Requested concerning the fixed stream of DDoS assaults whose origins have traced again to Stark Industries over the previous two years, Neculiti maintained Stark hasn’t obtained any official abuse studies about assaults coming from its networks.
“It was in all probability some sort of intelligent assault that we didn’t see, I don’t rule out this reality, as a result of we’ve a really massive variety of shoppers and our Web channels are fairly massive,” he mentioned. “However, on this state of affairs, sadly, nobody contacted us to report that there was an assault from our addresses; if somebody had contacted us, we’d have undoubtedly blocked the community information.”
DomainTools.com finds Ivan V. Neculiti was the proprietor of struggle[.]md, an internet site launched in 2008 that chronicled the historical past of a 1990 armed battle in Moldova referred to as the Transnistria Battle and the Moldo-Russian struggle.

An advert for struggle.md, circa 2009.
Transnistria is a breakaway pro-Russian area that declared itself a state in 1990, though it isn’t internationally acknowledged. The copyright on that web site credit the “MercenarieS TeaM,” which was at one time a Moldovan IT agency. Mr. Neculiti confirmed personally registering this area.
DON CHICHO & DFYZ
The info breach monitoring service Constella Intelligence studies that an Ivan V. Neculiti registered a number of on-line accounts beneath the e-mail deal with [email protected]. Cyber intelligence agency Intel 471 reveals this electronic mail deal with is tied to the username “dfyz” on greater than a half-dozen Russian language cybercrime boards since 2008. The consumer dfyz on Searchengines[.]ru in 2008 requested different discussion board members to assessment struggle.md, and mentioned they had been a part of the MercenarieS TeaM.
Again then, dfyz was promoting “bulletproof servers for any function,” that means the internet hosting firm would willfully ignore abuse complaints or police inquiries concerning the exercise of its clients.
DomainTools studies there are at the least 33 domains registered to [email protected]. A number of of those domains have Ivan Neculiti of their registration information, together with tracker-free[.]cn, which was registered to an Ivan Neculiti at [email protected] and referenced the MercenarieS TeaM in its authentic registration information.
Dfyz additionally used the nickname DonChicho, who likewise bought bulletproof internet hosting companies and entry to hacked Web servers. In 2014, a distinguished member of the Russian language cybercrime neighborhood Antichat filed a criticism in opposition to DonChicho, saying this consumer scammed them and had used the e-mail deal with [email protected].
The criticism mentioned DonChicho registered on Antichat from the Transnistria Web deal with 84.234.55[.]29. Looking out this deal with in Constella reveals it has been used to register simply 5 accounts on-line which were created over time, together with one at ask.ru, the place the consumer registered with the e-mail deal with [email protected]. Constella additionally returns for that electronic mail deal with a consumer by the identify “Ivan” at memoraleak.com and 000webhost.com.
Constella finds that the password most incessantly utilized by the e-mail deal with [email protected] was “filecast,” and that there are greater than 90 electronic mail addresses related to this password. Amongst them are roughly two dozen addresses with the identify “Neculiti” in them, in addition to the deal with help@donservers[.]ru.
Intel 471 says DonChicho posted to a number of Russian cybercrime boards that help@donservers[.]ru was his deal with, and that he logged into cybercrime boards virtually solely from Web addresses in Tiraspol, the capital of Transnistria. A assessment of DonChicho’s posts reveals this particular person was banned from a number of boards in 2014 for scamming different customers.
Cached copies of DonChicho’s self-importance area (donchicho[.]ru) present that in 2009 he was a spammer who peddled knockoff prescribed drugs by way of Rx-Promotion, as soon as one of many largest pharmacy spam moneymaking packages for Russian-speaking associates.
Mr. Neculiti informed KrebsOnSecurity he has by no means used the nickname DonChicho.
“I could guarantee you that I’ve no relation to DonChicho nor to his bulletproof servers,” he mentioned.
Under is a thoughts map that reveals the connections between the accounts talked about above.
Earlier this 12 months, NoName started massively hitting authorities and trade web sites in Moldova. A new report from Arbor Networks says the assaults started round March 6, when NoName alleged the federal government of Moldova was “longing for Russophobia.”
“Since early March, greater than 50 web sites have been focused, in keeping with posted ‘proof’ by the teams concerned in attacking the nation,” Arbor’s ASERT Staff wrote. “Whereas NoName seemingly initiated the ramp of assaults, a bunch of different DDoS hacktivists have joined the fray in claiming credit score for assaults throughout greater than 15 industries.”
CORRECTIV ACTION
The German impartial information outlet Correctiv.org final week printed a scathing investigative report on Stark Industries and MIRhosting, which notes that Ivan Neculiti operates his internet hosting firms with the assistance of his brother, Yuri.
The report factors out that Stark Industries continues to host a Russian disinformation information outlet known as “Latest Dependable Information” (RRN) that was sanctioned by the European Union in 2023 for spreading hyperlinks to propaganda blogs and faux European media and authorities web sites.
“The web site was not operating on computer systems in Moscow or St. Petersburg till lately, however in the course of the EU, within the Netherlands, on the computer systems of the Neculiti brothers,” Correctiv reporters wrote.
“After a request from this editorial group, a widely known service was put in that hides the precise net host,” the report continues. “Ivan Neculiti introduced that he had blocked the related entry and server following inside investigations. “We very a lot remorse that we’re solely now discovering out that certainly one of our clients is a sanctioned portal,” mentioned the corporate boss. Nonetheless, RRN continues to be accessible by way of its servers.”
Correctiv additionally factors to a January 2023 report from the Ukrainian authorities, which discovered servers from Stark Industries Options had been used as a part of a cyber assault on the Ukrainian information company “Ukrinform”. Correctiv notes the infamous hacker group Sandworm — a complicated persistent risk (APT) group operated by a cyberwarfare unit of Russia’s army intelligence service — was recognized by Ukrainian authorities authorities as accountable for that assault.
PEACE HOSTING?
Public information point out MIRhosting is predicated in The Netherlands and is operated by 37-year outdated Andrey Nesterenko, whose private web site says he’s an achieved live performance pianist who started performing publicly at a younger age.
DomainTools says mirhosting[.]com is registered to Mr. Nesterenko and to Innovation IT Options Corp, which lists addresses in London and in Nesterenko’s said hometown of Nizhny Novgorod, Russia.
That is fascinating as a result of in keeping with the guide Inside Cyber Warfare by Jeffrey Carr, Innovation IT Options Corp. was accountable for internet hosting StopGeorgia[.]ru, a hacktivist web site for organizing cyberattacks in opposition to Georgia that appeared on the similar time Russian forces invaded the previous Soviet nation in 2008. That battle was considered the primary struggle ever fought through which a notable cyberattack and an precise army engagement occurred concurrently.
Responding to questions from KrebsOnSecurity, Mr. Nesterenko mentioned he couldn’t say whether or not his community had ever hosted the StopGeorgia web site again in 2008 as a result of his firm didn’t hold information going again that far. However he mentioned Stark Industries Options is certainly certainly one of MIRhsoting’s colocation clients.
“Our relationship is only provider-customer,” Nesterenko mentioned. “Additionally they make the most of a number of suppliers and information facilities globally, so connecting them on to MIRhosting overlooks their broader community.”
“We take any report of malicious exercise significantly and are at all times open to info that may assist us determine and stop misuse of our infrastructure, whether or not involving Stark Industries or every other buyer,” Nesterenko continued. “In circumstances the place our companies are exploited for malicious functions, we collaborate absolutely with Dutch cyber police and different related authorities to research and take applicable measures. Nonetheless, we’ve but to obtain any actionable info past the article itself, which has not supplied us with enough element to determine or block malicious actors.”
In December 2022, safety agency Recorded Future profiled the phishing and credential harvesting infrastructure used for Russia-aligned espionage operations by a gaggle dubbed Blue Charlie (aka TAG-53), which has focused electronic mail accounts of nongovernmental organizations and suppose tanks, journalists, and authorities and protection officers.
Recorded Future discovered that nearly all of the Blue Charlie domains existed in simply ten completely different ISPs, with a big focus situated in two networks, certainly one of which was MIRhosting. Each Microsoft and the UK authorities assess that Blue Charlie is linked to the Russian risk exercise teams variously referred to as Callisto Group, COLDRIVER, and SEABORGIUM.
Mr. Nesterenko took exception to a narrative on that report from The Report, which is owned by Recorded Future.
“We’ve mentioned its contents with our buyer, Stark Industries,” he mentioned. “We perceive that they’ve initiated authorized proceedings in opposition to the web site in query, as they firmly imagine that the claims made are inaccurate.”
Recorded Future mentioned they up to date their story with feedback from Mr. Neculiti, however that they stand by their reporting.
Mr. Nesterenko’s LinkedIn profile says he was beforehand the overseas area gross sales supervisor at Serverius-as, a internet hosting firm in The Netherlands that continues to be in the identical information middle as MIRhosting.
In February, the Dutch police took 13 servers offline that had been utilized by the notorious LockBit ransomware group, which had initially bragged on its darknet web site that its dwelling base was in The Netherlands. Sources inform KrebsOnSecurity the servers seized by the Dutch police had been situated in Serverius’ information middle in Dronten, which can also be shared by MIRhosting.
Serverius-as didn’t reply to requests for remark. Nesterenko mentioned MIRhosting does use certainly one of Serverius’s information facilities for its operations within the Netherlands, alongside two different information facilities, however that the current incident involving the seizure of servers has no connection to MIRhosting.
“We’re legally prohibited by Dutch legislation and police laws from sharing info with third events concerning any communications we might have had,” he mentioned.
A February 2024 report from safety agency ESET discovered Serverius-as methods had been concerned in a sequence of focused phishing assaults by Russia-aligned teams in opposition to Ukrainian entities all through 2023. ESET noticed that after the spearphishing domains had been now not energetic, they had been transformed to selling rogue Web pharmacy web sites.
PEERING INTO THE VOID
A assessment of the Web deal with ranges lately added to the community operated by Stark Industries Options presents some perception into its buyer base, utilization, and possibly even true origins. Here’s a snapshot (PDF) of all Web deal with ranges introduced by Stark Industries to this point within the month of Could 2024 (this info was graciously collated by the community observability platform Kentik.com).
These information point out that the biggest portion of the IP area utilized by Stark is in The Netherlands, adopted by Germany and the USA. Stark says it’s linked to roughly 4,600 Web addresses that at present listing their possession as Comcast Cable Communications.
A assessment of these deal with ranges at spur.us reveals all of them are linked to an entity known as Proxyline, which is a sprawling proxy service primarily based in Russia that at present says it has greater than 1.6 million proxies globally which can be out there for hire.

Proxyline dot internet.
Reached for remark, Comcast mentioned the Web deal with ranges by no means did belong to Comcast, so it’s doubtless that Stark has been fudging the actual location of its routing bulletins in some circumstances.
Stark studies that it has greater than 67,000 Web addresses at Santa Clara, Calif.-based EGIhosting. Spur says the Stark addresses involving EGIhosting all map to Proxyline as effectively. EGIhosting didn’t reply to requests for remark.
EGIhosting manages Web addresses for the Cyprus-based internet hosting agency ITHOSTLINE LTD (aka HOSTLINE-LTD), which is represented all through Stark’s introduced Web ranges. Stark says it has greater than 21,000 Web addresses with HOSTLINE. Spur.us finds Proxyline addresses are particularly concentrated within the Stark ranges labeled ITHOSTLINE LTD, HOSTLINE-LTD, and Proline IT.
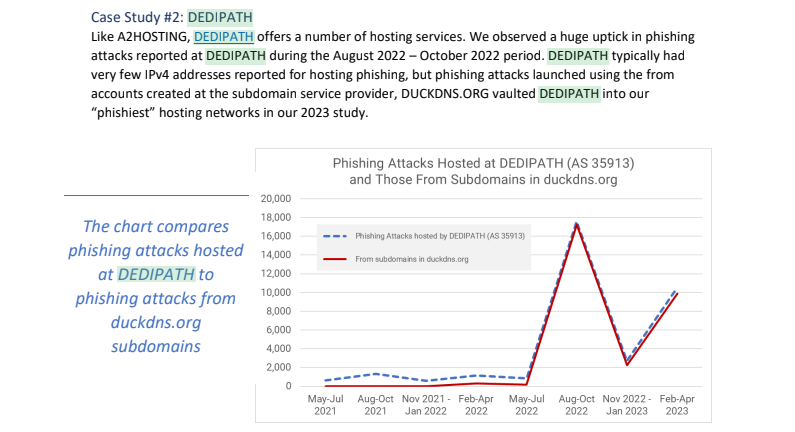
Stark’s community listing contains roughly 21,000 Web addresses at Hockessin, De. primarily based DediPath, which abruptly ceased operations with out warning in August 2023. Based on a phishing report launched final 12 months by Interisle Consulting, DediPath was the fourth commonest supply of phishing assaults within the 12 months ending Oct. 2022. Spur.us likewise finds that nearly the entire Stark deal with ranges marked “DediPath LLC” are tied to Proxyline.
Picture: Interisle Consulting.
Numerous the Web deal with ranges introduced by Stark in Could originate in India, and the names which can be self-assigned to many of those networks point out they had been beforehand used to ship massive volumes of spam for natural medicinal merchandise, with names like HerbalFarm, AdsChrome, Nutravo, Herbzoot and Herbalve.
The anti-spam group SpamHaus studies that lots of the Indian IP deal with ranges are related to identified “snowshoe spam,” a type of abuse that includes mass electronic mail campaigns unfold throughout a number of domains and IP addresses to weaken fame metrics and keep away from spam filters.
It’s not clear how a lot of Stark’s community deal with area traces its origins to Russia, however huge chunks of it lately belonged to a number of the oldest entities on the Russian Web (a.ok.a. “Runet”).
For instance, many Stark deal with ranges had been most lately assigned to a Russian authorities entity whose full identify is the “Federal State Autonomous Instructional Institution of Further Skilled Schooling Middle of Realization of State Instructional Coverage and Informational Applied sciences.”
A assessment of Web deal with ranges adjoining to this entity reveals an extended listing of Russian authorities organizations which can be a part of the Federal Guard Service of the Russian Federation. Wikipedia says the Federal Guard Service is a Russian federal authorities company involved with duties associated to safety of a number of high-ranking state officers, together with the President of Russia, in addition to sure federal properties. The company traces its origins to the USSR’s Ninth Directorate of the KGB, and later the presidential safety service.
Stark lately introduced the deal with vary 213.159.64.0/20 from April 27 to Could 1, and this vary was beforehand assigned to an historical ISP in St. Petersburg, RU known as the Laptop Applied sciences Institute Ltd.
Based on a submit on the Russian language webmaster discussion board searchengines[.]ru, the area for Laptop Applied sciences Institute — ctinet[.]ru — is the seventh-oldest area in your entire historical past of the Runet.
Curiously, Stark additionally lists massive tracts of Web addresses (near 48,000 in complete) assigned to a small ISP in Kharkiv, Ukraine known as NetAssist. Reached by way of electronic mail, the CEO of NetAssist Max Tulyev confirmed his firm gives quite a few companies to PQ Internet hosting.
“We colocate their gear in Warsaw, Madrid, Sofia and Thessaloniki, present them IP transit and IPv4 addresses,” Tulyev mentioned. “For his or her measurement, we obtain comparatively low variety of complains to their networks. I by no means seen something about their pro-Russian exercise or help of Russian hackers. It is vitally fascinating for me to see proofs of your accusations.”
Spur.us mapped your entire infrastructure of Proxyline, and located a couple of million proxies throughout a number of suppliers, however by far the largest focus was at Stark Industries Options. The full listing of Proxyline deal with ranges (.CSV) reveals two different ISPs seem repeatedly all through the listing. One is Kharkiv, Ukraine primarily based ITL LLC, often known as Data Expertise Laboratories Group, and Built-in Applied sciences Laboratory.
The second is a associated internet hosting firm in Miami, known as Inexperienced Floid LLC. Inexperienced Floid featured in a 2017 scoop by CNN, which profiled the corporate’s proprietor and quizzed him about Russian troll farms utilizing proxy networks on Inexperienced Floid and its father or mother agency ITL to masks disinformation efforts tied to the Kremlin’s Web Analysis Company (IRA). On the time, the IRA was utilizing Fb and different social media networks to unfold movies exhibiting police brutality in opposition to African Individuals in an effort to encourage protests throughout the USA.

Doug Madory, director of Web evaluation at Kentik, was capable of see at a excessive degree the highest sources and locations for site visitors traversing Stark’s community.
“Primarily based on our combination NetFlow, we see Iran as the highest vacation spot (35.1%) for site visitors emanating from Stark (AS44477),” Madory mentioned. “Particularly, the highest vacation spot is MTN Irancell, whereas the highest supply is Fb. This information helps the speculation that AS44477 homes proxy companies as Fb is blocked in Iran.”
On April 30, the safety agency Malwarebytes explored an intensive malware operation that targets company Web customers with malicious advertisements. Among the many websites used as lures in that marketing campaign had been pretend Wall Road Journal and CNN web sites that informed guests they had been required to put in a WSJ or CNN-branded browser extension (malware). Malwarebytes discovered a website identify central to that operation was hosted at Web addresses owned by Stark Industries.
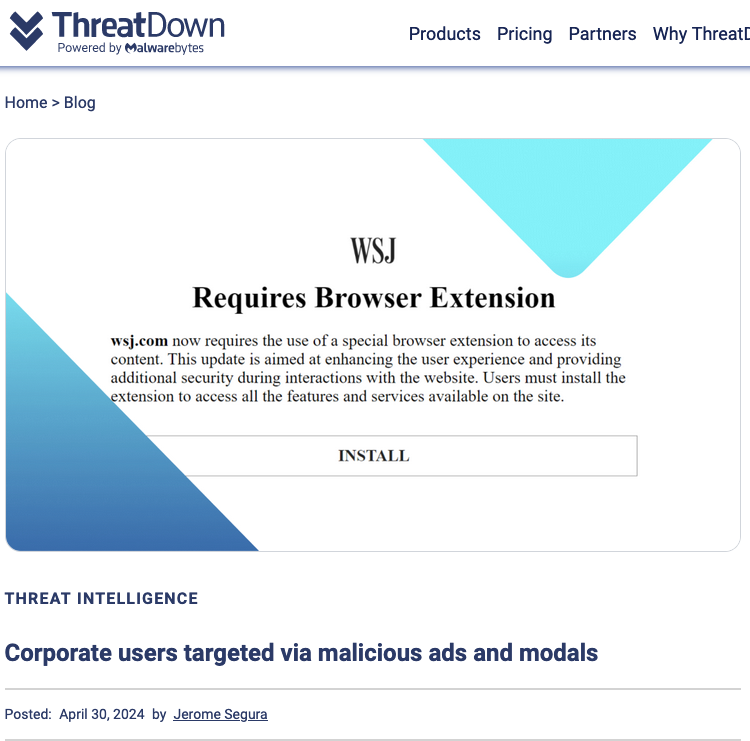
Picture: threatdown.com