The content material of this publish is solely the accountability of the writer. LevelBlue doesn’t undertake or endorse any of the views, positions, or info offered by the writer on this article.
Reminiscence forensics is a vital side of digital forensics, permitting investigators to investigate the risky reminiscence of a system to uncover proof of malicious exercise, detect hidden malware, and reconstruct system occasions. On this weblog, we’ll discover the world of reminiscence forensics utilizing two highly effective instruments: Fmem and LiME. We’ll delve into the fundamentals of reminiscence forensics, discover the options and capabilities of Fmem and LiME, and supply a step-by-step information on how one can use these instruments to investigate a reminiscence dump.
What’s Reminiscence Forensics?
Reminiscence forensics includes the evaluation of a system’s risky reminiscence to extract useful details about system state, working processes, and community connections. Such a evaluation is essential in incident response, malware evaluation, and digital forensics investigations. By analysing reminiscence, investigators can:
1. Detect Hidden Malware and Rootkits:
Reminiscence forensics allows investigators to uncover hidden malware and rootkits which may be actively working in a system’s reminiscence. Not like conventional antivirus software program that primarily scans the file system, reminiscence forensics instruments can determine malicious code and processes that try and evade detection by residing solely in reminiscence.
2. Establish Malicious Processes and Community Connections:
By analyzing the contents of a system’s reminiscence, forensic analysts can determine suspicious processes and community connections. This consists of processes which may be performing malicious actions reminiscent of knowledge exfiltration, privilege escalation, or community reconnaissance. Figuring out these malicious entities is essential for understanding the scope and affect of a safety incident.
3. Reconstruct System Occasions and Timelines:
Reminiscence forensics permits investigators to reconstruct the sequence of occasions that occurred on a system main as much as and through a safety incident. By analyzing reminiscence artifacts reminiscent of course of creation timestamps, community connection logs, and registry modifications saved in reminiscence, investigators can create an in depth timeline of actions, which aids in understanding the ways and strategies employed by attackers.
4. Extract Delicate Knowledge:
Risky knowledge, reminiscent of passwords, encryption keys, and different delicate info, could also be current in a system’s reminiscence throughout regular operation. Reminiscence forensics instruments can extract this knowledge from reminiscence dumps, offering useful proof for digital investigations. This info will be essential for understanding how attackers gained entry to delicate sources and for mitigating potential safety dangers.
Utilizing fmem for Reminiscence Seize:
fmem is a kernel module that creates a digital system, /dev/fmem, which permits direct entry to the bodily reminiscence of a system. This module is especially helpful for buying reminiscence dumps of a compromised system, even when the system is protected by Safe Boot or has disabled the flexibility to learn bodily reminiscence instantly.
Comply with these steps to seize reminiscence utilizing fmem: Obtain the fmem supply code from the official repository or bundle supervisor. The identical will be discovered right here.
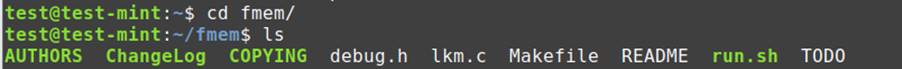
As soon as cloned into the repository, change listing to fmem utilizing cd command. You should use ls command to record the contents of the listing.
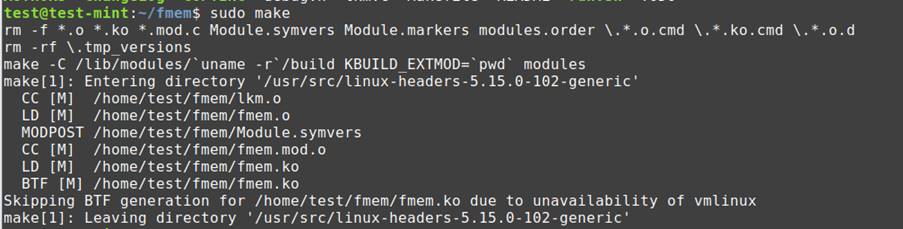
Compile and set up fmem on the goal Linux system:
As soon as you might be in fmem listing, use command “sudo make” to construct all the required libraries related to fmem from the supply code.
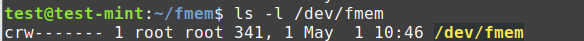
Verify if the /dev/fmem system has been created utilizing the next command: ls -l /dev/fmem
It is best to see one thing like this:
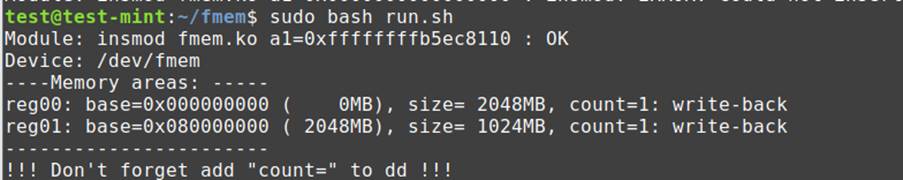
Now, to put in fmem, now we have to run the bash script in fmem listing. To make use of the identical you need to use sudo bash run.sh or sudo ./run.sh
Now to accumulate the reminiscence dump, you need to use a software like dd. Use the next command: sudo dd if=/dev/fmem of=memdump.uncooked
As soon as executed, it might take a while to finish the acquisition of reminiscence relying on RAM measurement. After the completion it shall present you a dialog field like this. You can too use different instructions specifying buffersize, dd if=/dev/fmem of=/residence/”username”/memdump.dd bs=1MB
After you have acquired the reminiscence dump, you possibly can analyze it utilizing LiME or different reminiscence forensics instruments. In our subsequent weblog, we’ll discover how one can analyze the reminiscence dump utilizing LiME.