Authored by Dexter Shin
Many authorities companies present their companies on-line for the comfort of their residents. Additionally, if this service could possibly be supplied by way of a cellular app, it could be very handy and accessible. However what occurs when malware pretends to be these companies?
McAfee Cell Analysis Workforce discovered an InfoStealer Android malware pretending to be a authorities company service in Bahrain. This malware pretends to be the official app of Bahrain and advertises that customers can renew or apply for driver’s licenses, visas, and ID playing cards on cellular. Customers who’re deceived by ads that they’re obtainable on cellular might be supplied with the required private data for these companies no doubt. They attain customers in numerous methods, together with Fb and SMS messages. Customers who usually are not aware of these assaults simply make the error of sending private data.
Detailed pretended app
In Bahrain, there’s a authorities company referred to as the Labour Market Regulatory Authority (LMRA). This company operates with full monetary and administrative independence below the steerage of a board of administrators chaired by the Minister of Labour. They supply a wide range of cellular companies, and most apps present just one service per app. Nevertheless, this faux app promotes offering a couple of service.
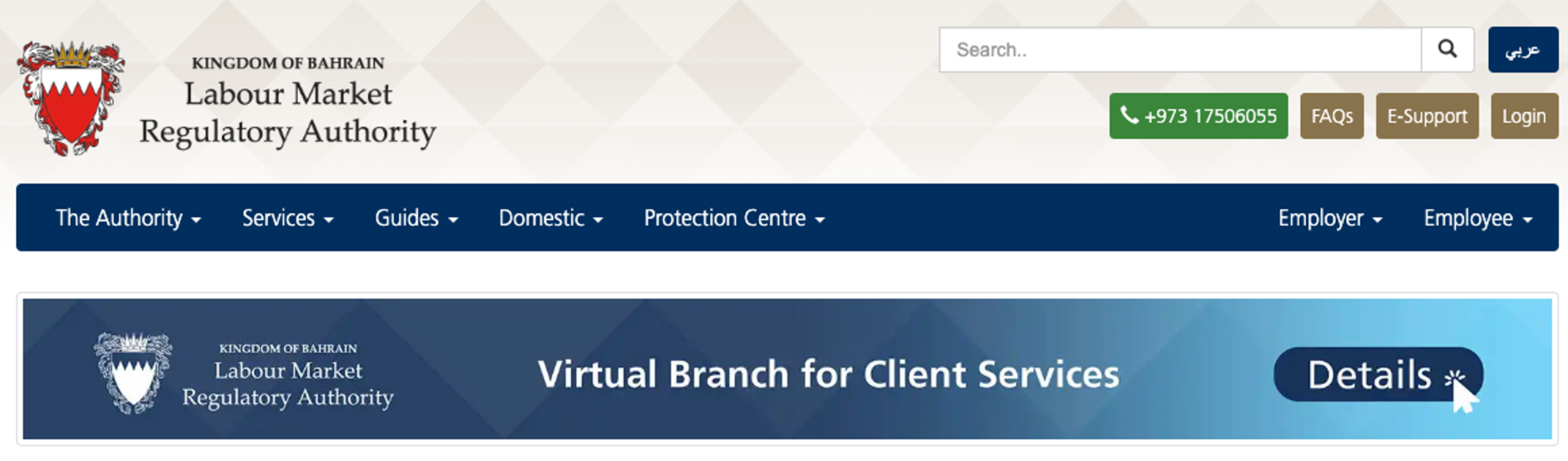
Determine 1. Legit official LMRA web site
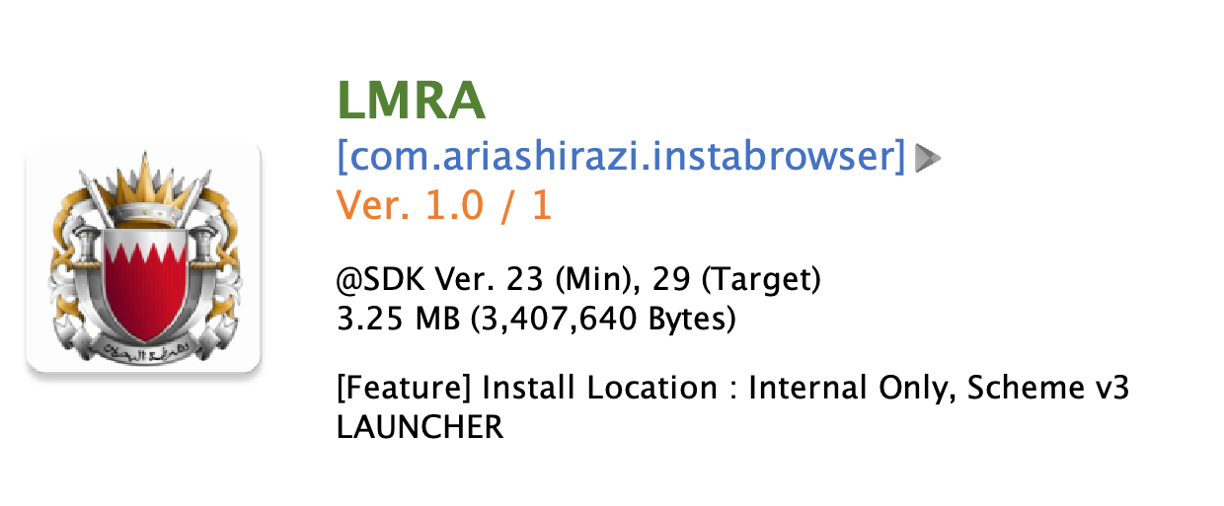
Determine 2. Faux app named LMRA
Excluding probably the most continuously discovered faux apps pretending LMRA, there are numerous faux apps included Financial institution of Bahrain and Kuwait (BBK), BenefitPay, a fintech firm in Bahrain, and even apps pretending to be associated to Bitcoin or loans. These apps use the identical methods because the LMRA faux apps to steal private data.

Determine 3. Varied faux apps utilizing the identical methods
From the kind of app that this malware pretends, we will guess that the aim is monetary fraud to make use of the private data it has stolen. Furthermore, somebody has been affected by this marketing campaign as proven within the image beneath.
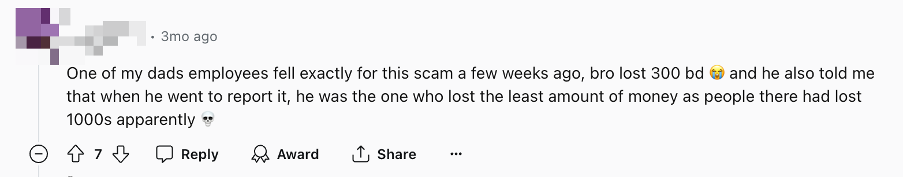
Determine 4. Victims of economic fraud (Supply: Reddit)
Distribution methodology
They distribute these apps utilizing Fb pages and SMS messages. Fb pages are faux and malware writer is consistently creating new pages. These pages direct customers to phishing websites, both WordPress weblog websites or customized websites designed to obtain apps.
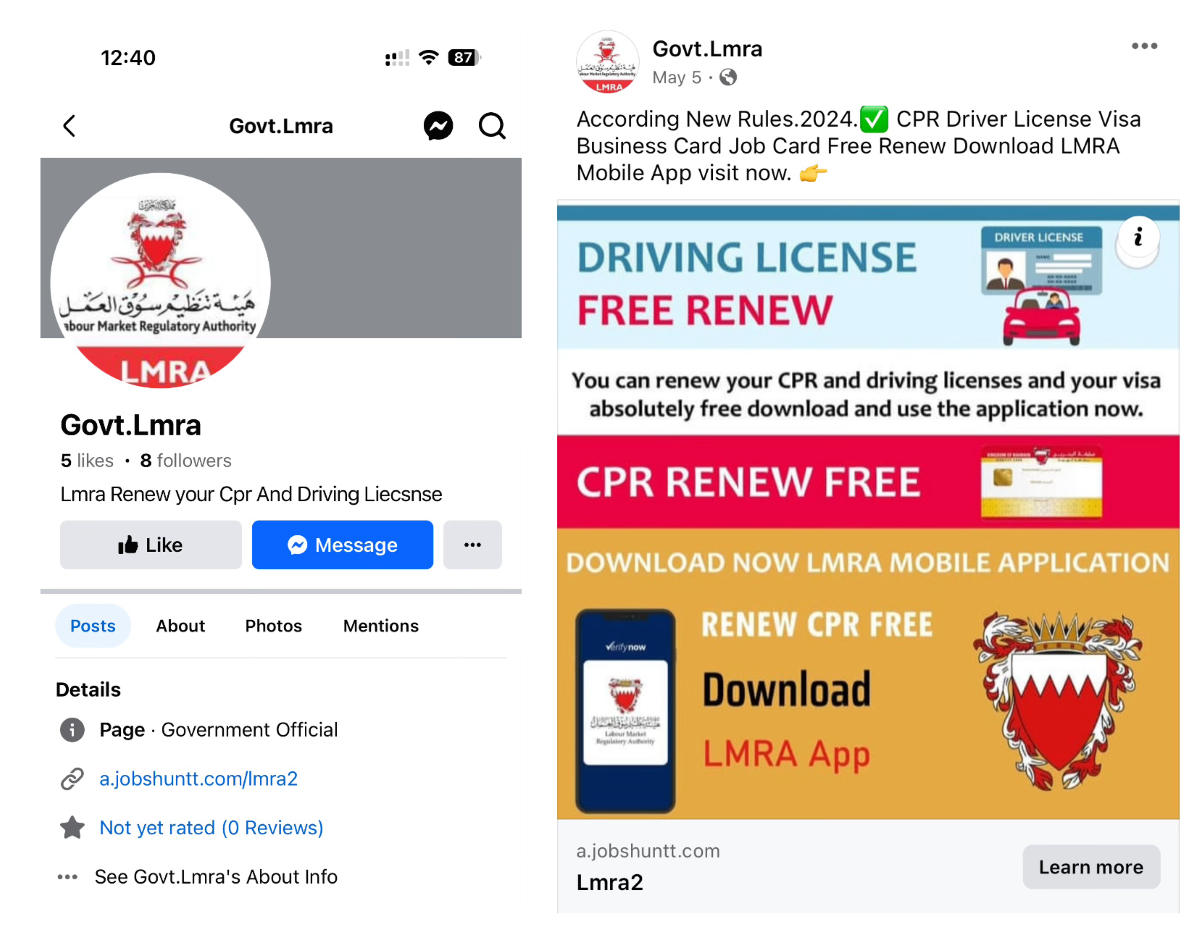
Determine 5. Fb profile and web page with a hyperlink to the phishing web site

Determine 6. One of many phishing websites designed to obtain app
Within the case of SMS, social engineering messages are despatched to trick customers into clicking a hyperlink in order that they really feel the necessity to urgently verify.
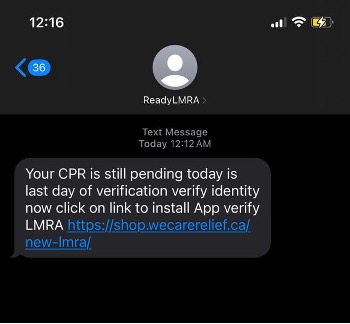
Determine 7. Phishing message utilizing SMS (Supply: Reddit)
What they need
When the consumer launches the app, the app reveals a big reliable icon for customers to be mistaken. And it asks for the CPR and telephone quantity. The CPR quantity is an unique 9-digit identifier given to every resident in Bahrain. There’s a “Confirm” button, however it’s merely a button to ship data to the C2 server. If customers enter their data, it goes on to the subsequent display with out verification. This step simply shops the knowledge for the subsequent step.
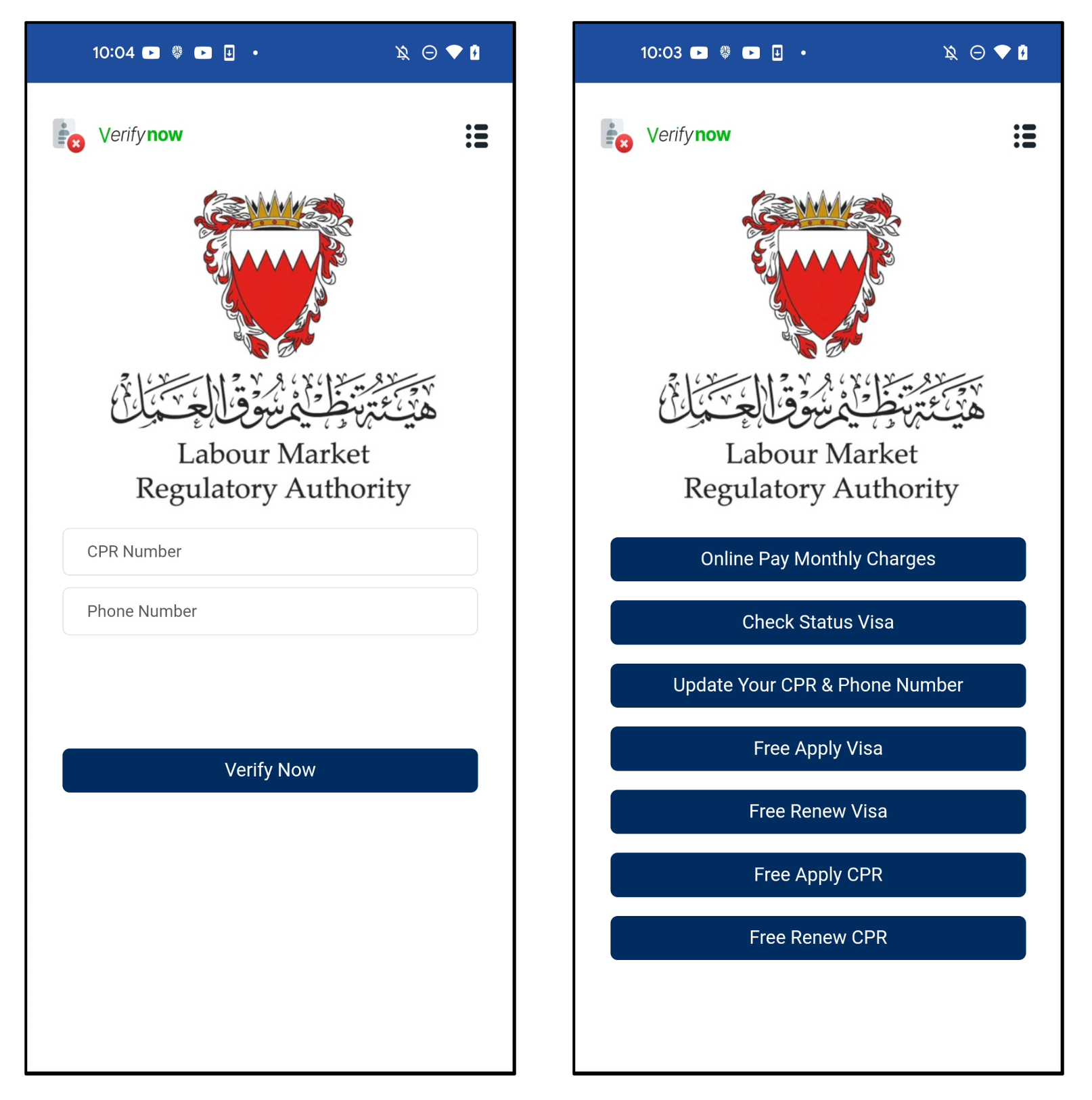
Determine 8. The primary display (left) and subsequent display of a faux app (proper)
There are numerous menus, however they’re all linked to the identical URL. The parameter worth is the CPR and telephone numbers enter by the consumer on the primary display.
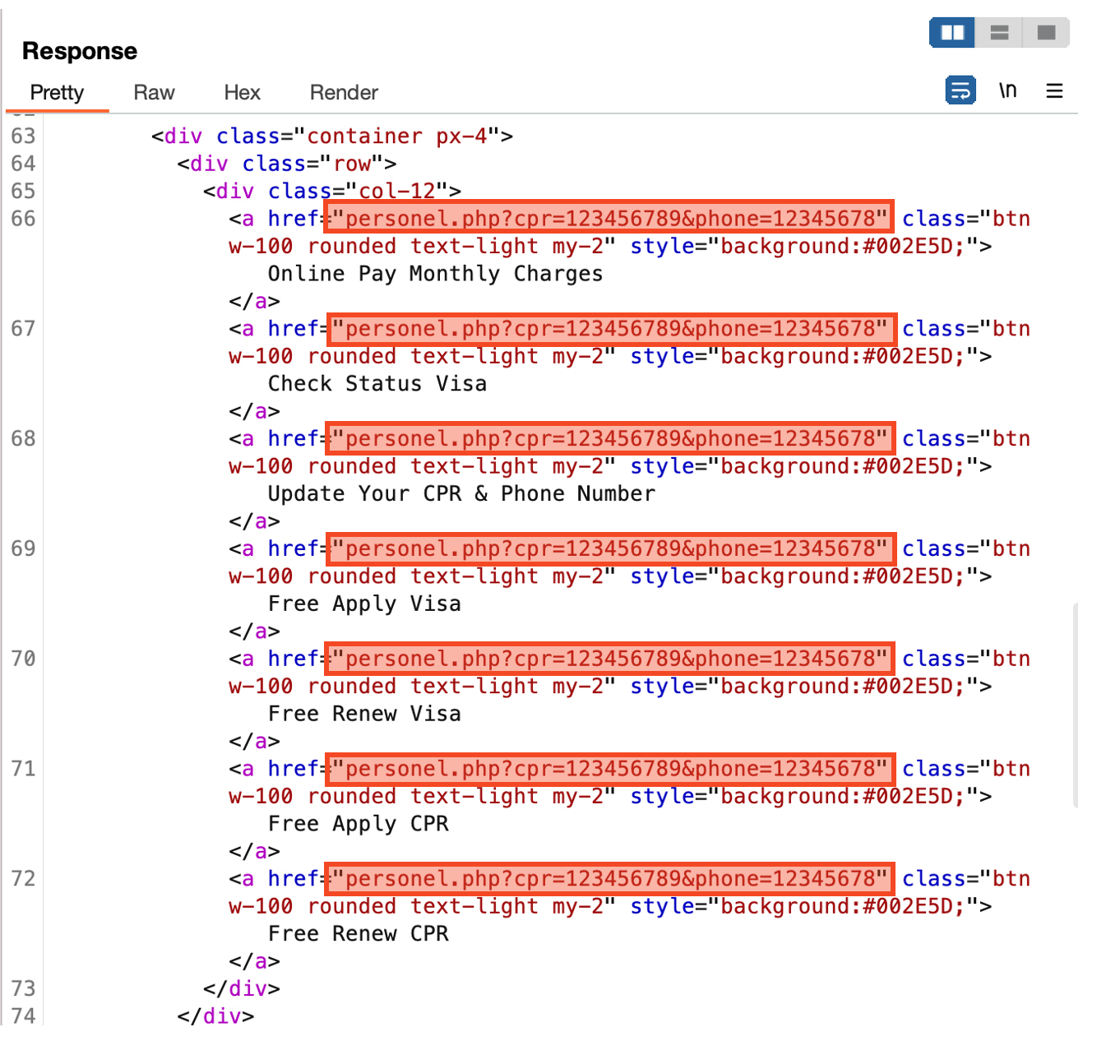
Determine 9. All menus are linked to the identical URL
The final web page asks for the consumer’s full identify, electronic mail, and date of beginning. After inputting the whole lot and clicking the “Ship” button, all data inputted to date might be despatched to the malware writer’s c2 server.
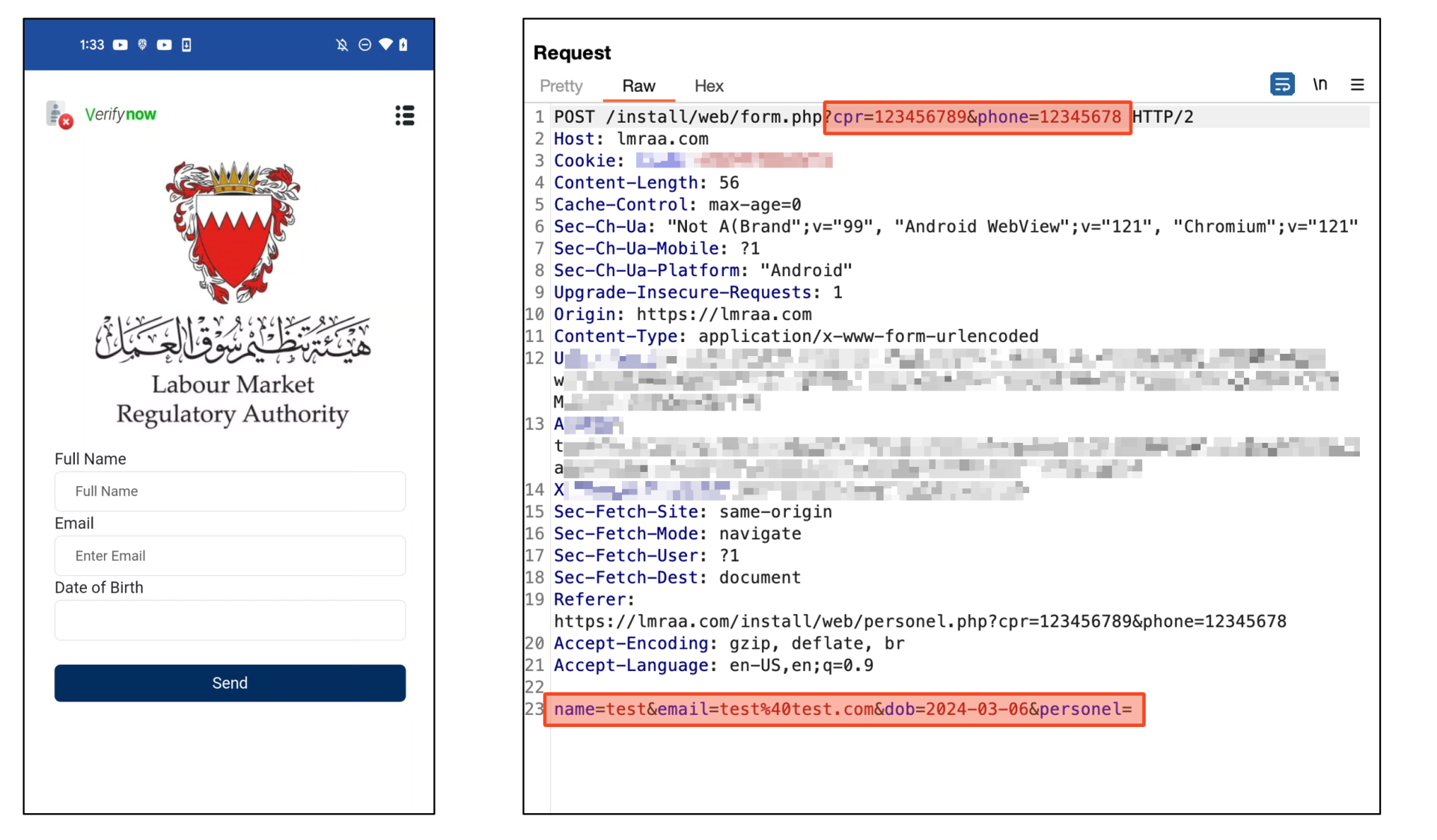
Determine 10. All knowledge despatched to C2 server
After sending, it reveals a completion web page to trick the consumer. It reveals a message saying you’ll obtain an electronic mail inside 24 hours. However it’s only a counter that decreases robotically. So, it does nothing after 24 hours. In different phrases, whereas customers are ready for the affirmation electronic mail for twenty-four hours, cybercriminals will exploit the stolen data to steal victims’ monetary property.
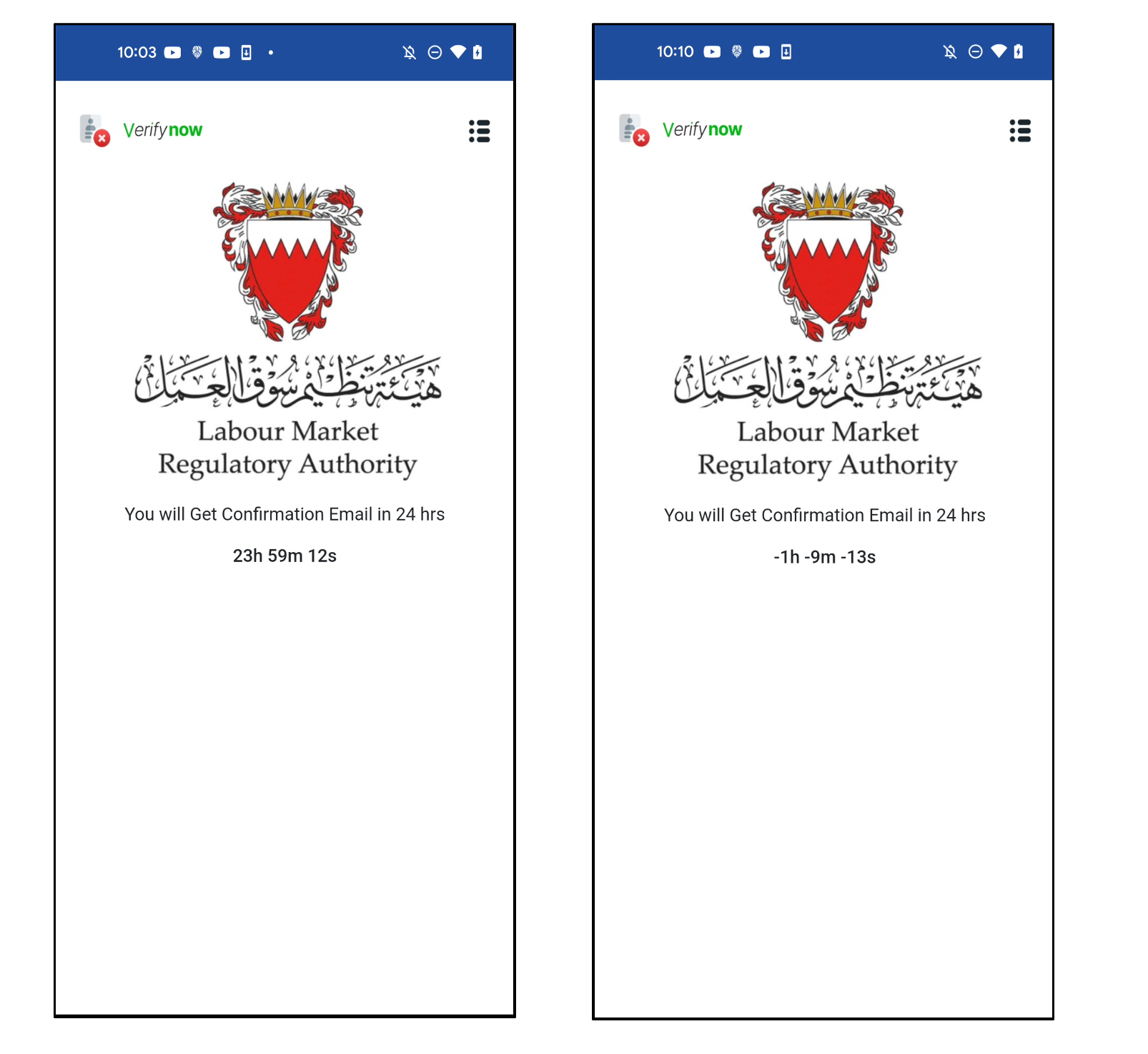
Determine 11. Completion web page to trick customers
As well as, they’ve a payload for stealing SMS. This app has a receiver that works when SMS is acquired. In order quickly as SMS comes, it sends an SMS message to the C2 server with out notifying the consumer.
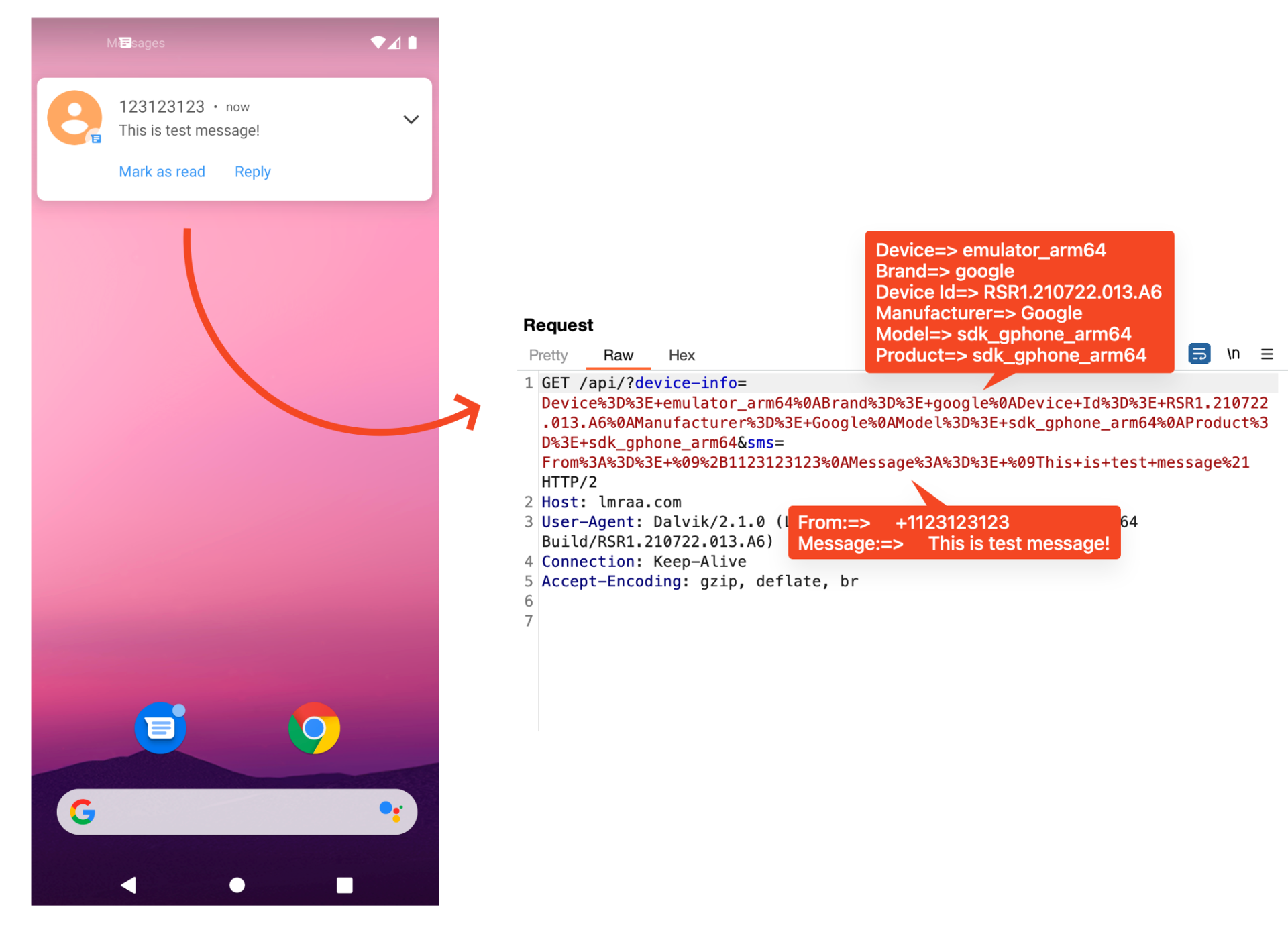
Determine 12. Payload for stealing SMS
Dynamic loading of phishing websites through Firebase
We confirmed that there are two forms of these apps. There’s a sort that implements a customized C2 server and receives knowledge instantly by way of internet API, and one other sort is an app that makes use of Firebase. Firebase is a backend service platform supplied by Google. Amongst many companies, Firestore can retailer knowledge as a database. This malware makes use of Firestore. As a result of it’s a reliable service supplied by Google, it’s troublesome to detect as a malicious URL.
For apps that use Firebase, dynamically load phishing URLs saved in Firestore. Subsequently, even when a phishing web site is blocked, it’s doable to reply rapidly to take care of already put in victims by altering the URL saved in Firestore.
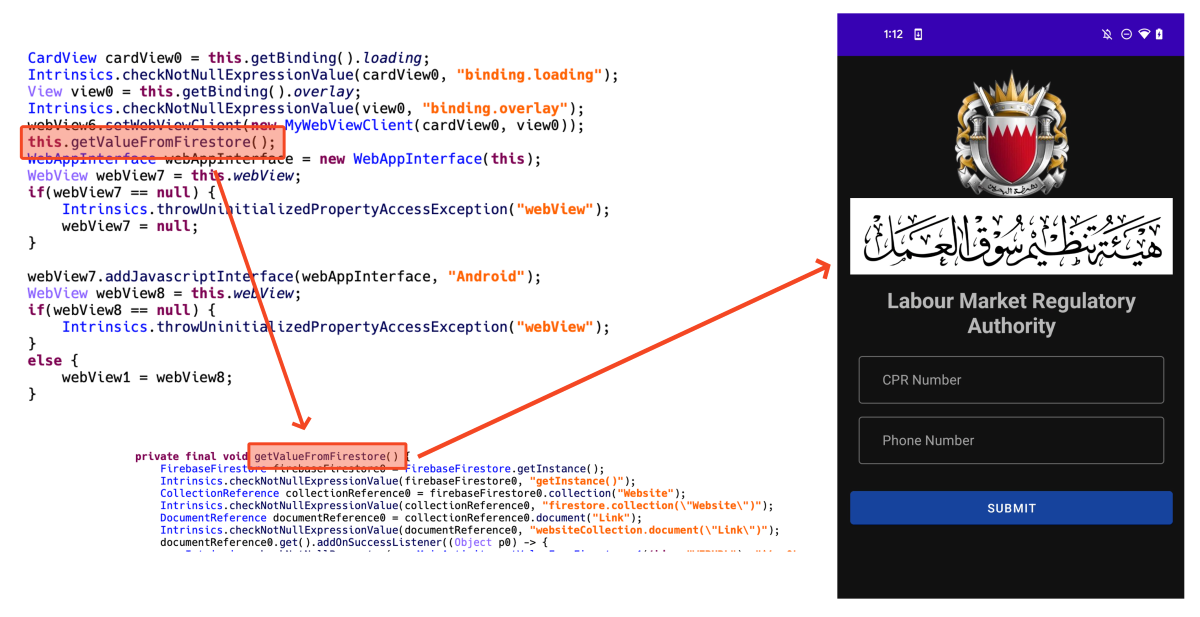
Determine 13. Dynamically loading phishing web site loaded in webview
We reported the Firebase URLs associated to this risk to Google they usually took immediate enforcement motion on them so they don’t seem to be obtainable anymore.
Conclusion
Based on our detection telemetry knowledge, there are 62 customers have already used this app in Bahrain. Nevertheless, since this knowledge is a quantity on the time of writing, this quantity is predicted to proceed to extend, contemplating that new Fb pages are nonetheless being actively created.
Latest malware tends to focus on particular international locations or customers somewhat than widespread assaults. These assaults could also be troublesome for common customers to tell apart as a result of malware precisely makes use of the components wanted by customers residing in a particular nation. So we advocate customers set up safe software program to guard their gadgets. Additionally, customers are inspired to obtain and use apps from official app shops like Google Play Retailer or Apple AppStore. In the event you can’t discover an app in these shops, you will need to obtain the app supplied on the official web site.
McAfee Cell Safety already detects this risk as Android/InfoStealer. For extra data, go to McAfee Cell Safety.
Indicators of Compromise (IOCs)
Samples:
| SHA256 | Bundle Title | App Title |
| 6f6d86e60814ad7c86949b7b5c212b83ab0c4da65f0a105693c48d9b5798136c | com.ariashirazi.instabrowser | LMRA |
| 5574c98c9df202ec7799c3feb87c374310fa49a99838e68eb43f5c08ca08392d | com.npra.bahrain.5 | LMRA Bahrain |
| b7424354c356561811e6af9d8f4f4e5b0bf6dfe8ad9d57f4c4e13b6c4eaccafb | com.npra.bahrain.5 | LMRA Bahrain |
| f9bdeca0e2057b0e334c849ff918bdbe49abd1056a285fed1239c9948040496a | com.lmra.9.lmranine | LMRA |
| bf22b5dfc369758b655dda8ae5d642c205bb192bbcc3a03ce654e6977e6df730 | com.stich.inches | Visa Replace |
| 8c8ffc01e6466a3e02a4842053aa872119adf8d48fd9acd686213e158a8377ba | com.ariashirazi.instabrowser | EasyLoan |
| 164fafa8a48575973eee3a33ee9434ea07bd48e18aa360a979cc7fb16a0da819 | com.ariashirazi.instabrowser | BTC Flasher |
| 94959b8c811fdcfae7c40778811a2fcc4c84fbdb8cde483abd1af9431fc84b44 | com.ariashirazi.instabrowser | BenefitPay |
| d4d0b7660e90be081979bfbc27bbf70d182ff1accd829300255cae0cb10fe546 | com.lymors.lulumoney | BBK Mortgage App |
Domains:
- https[://]lmraa.com
- https[://]lmjbfv.web site
- https[://]dbjiud.web site
- https[://]a.jobshuntt.com
- https[://]store.wecarerelief.ca
Firebase (for C2):
- https[://]npra-5.firebaseio.com
- https[://]lmra9-38b17.firebaseio.com
- https[://]practice-8e048.firebaseio.com


