(Dave Hoeek/Shutterstock)
With the Nationwide Institute of Requirements and Know-how (NIST) set to publish the primary Put up Quantum Cryptography (PQC) Requirements in just a few weeks, consideration is shifting to easy methods to put the brand new quantum-resistant algorithms into follow. Certainly, the variety of corporations with practices to assist others implement PQC is mushrooming and incorporates acquainted (IBM, Deloitte, et al.) and unfamiliar names (QuSecure, SandboxAQ, and so forth.).
The Migration to Put up-Quantum Cryptography challenge, being run out of NIST’s Nationwide Cybersecurity Middle of Excellence (NCCoE), is working at full-tilt and contains on the order of 40 business members.
In its personal phrases, “The challenge will interact business in demonstrating use of automated discovery instruments to establish all cases of public-key algorithm use in an instance community infrastructure’s laptop and communications {hardware}, working programs, software applications, communications protocols, key infrastructures, and entry management mechanisms. The algorithm employed and its goal can be recognized for every affected infrastructure element.”

Attending to that objective stays a WIP that began with NIST’s PQC program in 2016. NIST scientist Dustin Moody leads the PQC challenge and talked with HPCwire about the necessity to take publish quantum cryptography significantly now, not later.
“The US authorities is mandating their companies to it, however business in addition to going to should be doing this migration. The migration is just not going to be straightforward [and] it’s not going to be ache free,” mentioned Moody, whose Ph.D. specialised in elliptic curves, a generally used base for encryption. “Fairly often, you’re going to want to make use of subtle instruments which can be being developed to help with that. Additionally discuss to your distributors, your CIOs, your CEOs to ensure they’re conscious and that they’re planning for budgets to do that. Simply because a quantum laptop [able to decrypt] isn’t going to be constructed for, who is aware of, possibly 15 years, they could suppose I can simply put this off, however understanding that menace is coming prior to than you understand is necessary.”
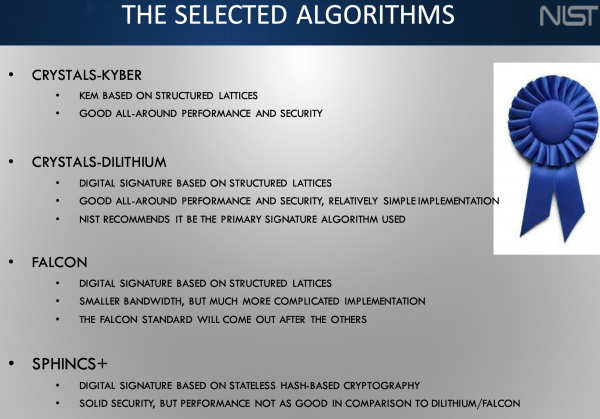
Estimates differ wildly across the dimension of the menace however maybe 20 billion units will should be up to date with PQC safeguarding. NIST has held 4 rounds of submissions and the primary set of requirements will embody algorithms chosen the primary three. These are the principle weapons in opposition to quantum decryption assault. The following spherical seeks to supply alternate options and, in some cases, considerably much less burdensome computational traits.
The dialogue with Moody was wide-ranging, if maybe just a little dry. He covers PQC technique and progress and the necessity to monitor the fixed circulation of recent quantum algorithms. Shor’s algorithm is the well-known menace however others are percolating. He notes that many submitted algorithms broke down beneath testing however says to not make a lot of that as that’s the character of the requirements improvement course of. He talks about pursuing cryptoagility and presents just a few broad tips about preparation.
Moody additionally touched on geopolitcal rivalries amid what has been a typically collaborative worldwide effort.
“There are some exceptions like China by no means trusting the USA. They’re creating their very own PQC requirements. They’re really very, similar to the algorithms [we’re using] however they have been chosen internally. Russia has been doing their very own factor, they don’t actually talk with the remainder of the world very a lot. I don’t have loads of info on what they’re doing. China, despite the fact that they’re doing their very own requirements, did have researchers take part within the course of; they hosted one of many workshops within the area just a few years again. So the group is sufficiently small that individuals are excellent at working collectively, even when generally the nation will develop their very own requirements,” mentioned Moody.
How quickly quantum computer systems will really be capable of decrypt present RSA codes is way from clear, however early confidence that might be many many years has diminished. In case you’re on the lookout for an excellent primer on the PQS menace, he really useful the Quantum Deal with Timeline Report launched in December by the International Threat Institute (GRI) as one (figures from its research beneath).
HPCwire: Let’s discuss just a little bit concerning the menace. How large is it and when do we have to fear
Dustin Moody: Nicely, cryptographers have identified for just a few many years that if we’re in a position to construct a sufficiently big quantum laptop, it is going to threaten all the public key crypto programs that which we use at the moment. So it’s a it’s a severe menace. We don’t know when a quantum laptop can be constructed that’s giant sufficient to assault present ranges of safety. There’s been estimates of 10 to fifteen years, however you already know, no one is aware of for sure. Now we have seen progress in corporations constructing quantum computer systems — programs from IBM and Google, for instance, are getting bigger and bigger. So that is positively a menace to take significantly, particularly as a result of you’ll be able to’t simply wait till the quantum laptop is constructed after which say now we’ll fear about the issue. We have to clear up this 10 to fifteen years prematurely to guard your info for a very long time. There’s a menace of harvest-now-decrypt-later that helps you perceive that.
HPCwire: Marco Pistoia, who leads quantum analysis for JPMorgan Chase, mentioned he’d seen a research suggesting as few as 1300 or so logical qubits would possibly be capable of break standard RSA code, though it will take six months to take action. That was a 12 months in the past. It does seem to be our potential to execute Shor’s algorithm on these programs is bettering, not simply the brute drive, however our cleverness in getting the algorithm to run.
Dustin Moody: Yep, that’s true. And it’ll take loads of logical qubits. So we’re not there but. However yeah, progress has been made. It’s important to clear up the issue solved and migrate to new options earlier than we ever get to that time,
HPCwire: We are likely to concentrate on Shor’s algorithm as a result of it’s a direct menace to the present encryption strategies. Are there others within the wings that we must be nervous about?
Dustin Moody: There’s numerous quantum algorithms that we’re conscious of, Shor being certainly one of them, Grover’s being one other one which has an affect on cryptography. However there’s loads of different quantum algorithms that do attention-grabbing issues. So every time anybody is designing the crypto system, they’ve to try all these and see in the event that they seem like they may assault the system in any means? There’s sort of an inventory of I don’t know, possibly round 15 or in order that probably folks must sort of take a look at him and work out, do I want to fret about these.
HPCwire: Does NIST have that checklist someplace?
Dustin Moody: There was a man at NIST who stored up such an inventory. I believe he’s at Microsoft, now. It’s been a short while, however he maintained one thing referred to as the Quantum Algorithms Zoo.
HPCwire: Let’s get again to the NIST effort to develop quantum-resistant algorithms. As I perceive it, the method started being round 2016 has gone by way of this iterative course of the place you invite submissions of potential quantum resistant algorithms from the group, then take a look at them and provide you with some choices; there have been three rounds accomplished and within the means of turning into requirements, with an ongoing fourth spherical. Stroll me by way of the challenge and progress.
Dustin Moody: So these sorts of cryptographic competitions have been accomplished previously to pick out a few of the algorithms that we use at the moment. [So far] a broadly used block cypher was chosen by way of a contest. Extra just lately a hash operate. Again in 2016, we determined to do certainly one of these [competitions] for brand spanking new publish quantum algorithms that we would have liked requirements for. We let the group learn about that. They’re all excited and we obtained 82 submissions of which 69 met sort of the necessities that we’d got down to be concerned. Then we had a course of that over six or seven years [during which] we evaluated them going by way of a interval of rounds. In every spherical, we went additional all the way down to essentially the most promising to advance the tons of labor occurring in there, each internally at NIST, and by the cryptographic group, doing analysis and benchmarks and experiments and every little thing.
The third spherical had seven finalists and eight alternate concluded in July of 2022, the place we introduced gadgets that we might be standardizing consequently, that included one encryption algorithm and three signature algorithms. We did additionally maintain just a few encryption algorithms on right into a fourth spherical for additional research. They weren’t fairly able to be chosen for standardization. That fourth spherical remains to be ongoing and can most likely finish as this fall, and we’ll decide one or two of these to additionally standardize. We’ll have two or three encryption [methods] and three signatures as nicely.
HPCwire: It seems like a comparatively easy course of?
Dustin Moody: That course of obtained loads of consideration from the group. Numerous the algorithms ended up being damaged, some late within the course of — that’s sort of the character of how this factor works. That’s the place we are actually. We’re nearly accomplished writing the requirements for the primary ones that we chosen, our anticipated date is publishing them this summer season. The fourth spherical will finish this fall, after which we’ll write requirements for these that can take one other 12 months or two.
We even have ongoing work to pick out just a few extra digital signature algorithms as nicely. The explanation for that’s so lots of the algorithms we chosen are primarily based on what are referred to as lattices; they’re essentially the most promising household, [with] good efficiency, good safety. And for signatures, we had two primarily based on lattices, after which one not primarily based on lattices. The one which wasn’t primarily based on lattices — it’s referred to as SPHINCS+ — seems to be greater and slower. So if purposes wanted to make use of it, it may not be perfect for them. We needed to have a backup not primarily based on lattices that would get used simply. That’s what this ongoing digital signature course of is about [and] we’re encouraging researchers to attempt to design new options that aren’t primarily based on lattices which can be higher performing.
HPCwire: When NIST assesses these algorithms, it should look to see what number of computational sources are required to run them?
Dustin Moody: There’s particular analysis standards that we take a look at. Primary is safety. Quantity two is efficiency. And quantity three is that this laundry checklist of every little thing else. However we work internally at NIST, we’ve got a group of consultants and attempt to work with cryptography and business consultants around the globe who’re independently doing it. However generally we’re doing joint analysis with them within the area.
Safety has a large variety of methods to have a look at it. There’s the theoretical safety, the place you’re making an attempt to create safety proofs the place you’re making an attempt to say, ‘should you can break my crypto system, then you’ll be able to break this difficult mathematical downside.’ And we can provide a proof for that and since that tough mathematical downside has been studied, that provides us just a little bit extra confidence. Then it will get sophisticated as a result of we’re used to doing this with classical computer systems and how they’ll assault issues. However now we’ve got to have a look at how can quantum computer systems assault issues they usually don’t but exist. We don’t know their efficiency. capabilities. So we’ve got to extrapolate and do the very best that we are able to. But it surely’s all thrown into the combination.
Sometimes, you don’t find yourself needing supercomputers. You’re in a position to analyze how lengthy would the assaults take, what number of sources they take, should you have been to totally tried to interrupt the safety parameters at present ranges. The parameters are chosen in order that it’s [practically] infeasible to take action. You possibly can work out, if I have been to interrupt this, it will take, you already know, 100 years, so there’s no use in really making an attempt to try this until you sort of discover a breakthrough to discover a completely different means. (See descriptive checklist of NIST strengths classes at finish of article)
HPCwire: Do you take a look at on at the moment’s NISQ (near-term intermediate scale quantum) computer systems?
Dustin Moody: They’re too small proper now to essentially have any affect in how will a bigger quantum laptop fare in opposition to concrete parameters chosen at excessive sufficient safety ranges. So it’s extra theoretical, once you’re determining how a lot sources it will take.
HPCwire: So summarizing just a little bit, you suppose within the fall you’ll end this final fourth spherical. These would all be candidates for requirements, which then anybody might use for incorporation into encryption schemes that might be quantum laptop resistant.
Dustin Moody: That’s right. The principle ones that we anticipate to make use of have been already chosen in our first batch. So these are sort of the first ones, most individuals will use these. However we have to have some backups in case you already know, somebody comes up with a brand new breakthrough.
HPCwire: When you choose them do you intentionally have a variety when it comes to computational necessities, realizing that not everybody goes to have supercomputers at their doorstep. Many organizations might have to make use of extra modest sources when working these encryption codes. So folks might decide and select just a little bit primarily based on the computational necessities.
Dustin Moody: Sure, there’s a variety of safety classes from one to 5. Class 5 has the best safety, however efficiency is impacted. So there’s a commerce off. We embrace parameters for classes one, three, a 5 so folks can select the one which’s greatest fitted to their wants.
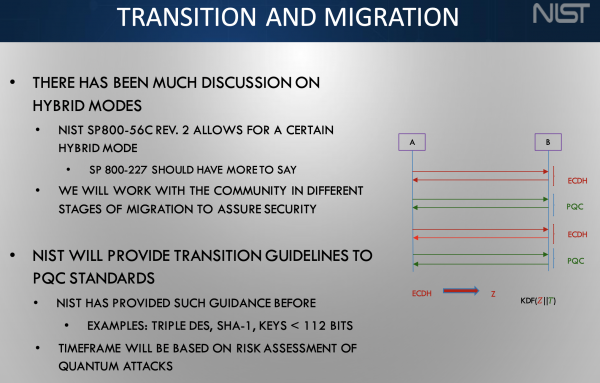
 HPCwire: Are you able to discuss just a little bit concerning the Migration to PQC challenge, which can be I imagine in NIST initiative to develop quite a lot of instruments for implementingPQC What’s your involvement? How is that going?
HPCwire: Are you able to discuss just a little bit concerning the Migration to PQC challenge, which can be I imagine in NIST initiative to develop quite a lot of instruments for implementingPQC What’s your involvement? How is that going?
Dustin Moody: That challenge is being run by NIST’s Nationwide Cybersecurity Middle of Excellence (NCCoE). I’m not one of many managers however I attend all of the conferences and I’m there to help what goes on. They’ve collaborated with…I believe the checklist is up 40 or 50 business companions and the checklist is on their web site. It’s a extremely sturdy collaboration. Numerous these corporations on their very own would usually be competing with every however right here, they’re all working for the widespread good of creating the migration as easy as doable, getting expertise creating instruments that individuals are going to want to do cryptographic inventories. That’s sort of one of many first steps that a corporation goes to want to do. Making an attempt to ensure every little thing might be interoperable. What classes can we study as we. Some individuals are additional alongside than others and the way can we share that info greatest? It’s actually good to have weekly calls, [and] we maintain occasions now and again. Principally these business collaborators are driving it and speaking with one another and we simply sort of arrange them collectively and assist them to maintain transferring.
HPCwire: Is there any effort to construct greatest practices on this space? One thing that that NIST and these collaborators from business and academia and DOE and DOD might all present? It will be maybe have the NIST stamp of authority on greatest practices for implementing quantum resistant cryptography.
Dustin Moody: Nicely, the requirements that my group is writing, and people are written by NIST and people are the algorithms that folks will implement. Then they’ll additionally then get examined and validated by a few of our labs at NIST. The migration challenge is producing paperwork, in a collection (NIST SP 1800-38A, NIST SP 1800-38B, NIST SP 1800-38C) and people are up to date now and again, the place they’re sharing what they’ve discovered and placing greatest follow on this. They’re NIST paperwork, written collectively with the NIST group and with these collaborators to share what they’ve obtained to date.
HPCwire: What can the potential consumer group do to be concerned? I understand the challenge is sort of mature, it’s been round for some time, and also you’ve obtained heaps of people that who’ve been concerned already. Are we on the stage the place the principle members are working with one another and NIST in creating these algorithms, and it’s now a matter of form of monitoring the instruments that come out.
Dustin Moody: I’d say each group must be turning into educated on understanding the quantum menace, realizing what’s occurring with standardization, realizing that you just’re going to want emigrate, and what that’s going to contain your group. It’s not going to be straightforward and ache free. So planning forward, and all that. In the event that they wish to be part of that that collaboration (Migration to PQC), individuals are nonetheless becoming a member of now and again and it’s nonetheless open if they’ve one thing that they’ve obtained to share. However for many organizations or teams, it’s going to be simply making an attempt to create your plan getting ready for the migration. We would like you to attend until the ultimate requirements are revealed, so that you’re not implementing the one thing that’s 99% the ultimate commonplace, we would like you to attend till that’s there, however you’ll be able to put together now.
HPCwire: When will they be remaining?
Dustin Moody: Of the 4 that we chosen, three of them. We put out draft requirements a 12 months in the past, obtained public suggestions, and have been revising since. The ultimate variations are going to be revealed this summer season. We don’t have a precise date, however it is going to, it’ll be this summer season.
HPCwire: At that time, will quite a lot of necessities will come round utilizing these algorithms, for instance within the U.S. authorities and maybe in business requiring compliance?
Dustin Moody: Technically NIST isn’t a regulatory company. So sure, US authorities can. I believe the OMB says that every one companies want to make use of our requirements. So the federal authorities has to make use of the requirements that we use for cryptography, however we all know {that a} wider viewers business in the USA and globally tends to make use of the algorithms that we standardized as nicely.
HPCwire: We’re in a world wherein geopolitical tensions are actual. Are we nervous about rivals from China or Russia, or different competing nations not sharing their advances? Or is the cryptoanalyst group sufficiently small that these sorts of issues should not more likely to occur as a result of the folks know one another?
 Dustin Moody: There’s a actual geopolitical menace when it comes to who will get the quantum laptop quickest. If China develops that they usually’re in a position to break into our cryptography, that’s a that’s an actual menace. When it comes to designing the algorithms and making the requirements, it’s been a really cooperative effort internationally. Trade advantages when lots of people are utilizing the identical algorithms everywhere in the world. And we’ve seen different nations in international requirements organizations say they’re going to make use of the algorithms that have been concerned in our course of.
Dustin Moody: There’s a actual geopolitical menace when it comes to who will get the quantum laptop quickest. If China develops that they usually’re in a position to break into our cryptography, that’s a that’s an actual menace. When it comes to designing the algorithms and making the requirements, it’s been a really cooperative effort internationally. Trade advantages when lots of people are utilizing the identical algorithms everywhere in the world. And we’ve seen different nations in international requirements organizations say they’re going to make use of the algorithms that have been concerned in our course of.
There are some exceptions like China by no means trusting the USA. They’re creating their very own PQC requirements. They’re really very, similar to the algorithms [we’re using] however they have been chosen internally. Russia has been doing their very own factor, they don’t actually talk with the remainder of the world very a lot. I don’t have loads of info on what they’re doing. China, despite the fact that they’re doing their very own requirements, did have researchers take part within the course of; they hosted one of many workshops within the area just a few years again. So the group is sufficiently small that individuals are excellent at working collectively, even when generally the nation will develop their very own requirements.
HPCwire: How did you become involved in cryptography? What drew you into this area?
Dustin Moody: Nicely, I like math and the mathematics I used to be learning has some purposes in cryptography, particularly, one thing referred to as elliptic curves, and there’s crypto programs we use at the moment which can be primarily based on the curve, which is that this stunning mathematical object that most likely nobody ever thought they’d be of any use within the in the true world. But it surely seems they’re for cryptography. In order that’s sort of my hook into cryptography.
I ended up at NIST as a result of NIST has elliptic curve cryptography requirements. I didn’t know something about publish quantum cryptography. Round 2014, my boss mentioned, we’re going to place you on this challenge coping with publish quantum cryptography and I used to be like, ‘What’s this? I’ve no concept what that is.’ Inside a few years, it sort of actually took off and grew and has turn out to be this excessive precedence for the USA authorities. It’s been a sort of a enjoyable journey to be on.
HPCwire: Wunwell the PQC challenge simply proceed or will it wrap up sooner or later?
Dustin Moody: We’ll proceed for plenty of years. We nonetheless have the fourth spherical to complete. We’re nonetheless doing this extra digital signature course of, which can take a number of extra years. However then once more, each every little thing we do sooner or later wants to guard in opposition to quantum computer systems. So these preliminary requirements will get revealed, they’ll be accomplished sooner or later, however all future cryptography requirements should take the quantum menace under consideration. So it’s sort of inbuilt that we’ve got to maintain going for the longer term.
HPCwire: When you discuss to the seller group, all of them say, “Encryption has been applied in such a haphazard means throughout programs that it’s all over the place, and that in merely discovering the place it exists in all these issues is tough.” The true objective, they argue, must be to maneuver to a extra modular predictable strategy. Is there a means NIST can affect that? Or the number of the algorithms can affect that?
Dustin Moody: Yes, and no. It’s very difficult. That concept you’re speaking about, generally the phrase cryptoagility will get thrown on the market in that course. Lots of people are speaking about, okay, we’re going to want emigrate these algorithms, this is a chance to revamp programs and protocols, possibly we are able to do it just a little bit extra intelligently than we did previously. On the identical time, it’s tough to try this, since you’ve obtained so many interconnected items doing so many issues. So it’s difficult to do, however we’re encouraging folks and having plenty of conversations like with the migration and PQC challenge. We’re encouraging folks to consider this, to revamp programs and protocols once you’re designing your purposes. Realizing I have to transition to those algorithms, possibly I can redesign my system in order that if I have to improve once more, sooner or later, it’ll be a lot simpler to do. I can maintain observe of the place my cryptography is, what occurs once I’m utilizing it, what info and defending. I hope that we’ll get some profit out of this migration, however it’s, it’s actually going to be very tough, sophisticated and painful as nicely.
HPCwire: Do you will have an off the highest of your head guidelines form of 5 issues you need to be excited about now to arrange for publish quantum cryptography?
Dustin Moody: I’d say primary, simply know that the migration is coming. The US authorities is mandating their companies to it, however business in addition to going to should be doing this migration. The migration is just not going to be straightforward, it’s not going to be ache free. You need to be educating your self as to what PQC is, the entire quantum menace, and beginning to determine, the place are you utilizing cryptography, what info is protected with cryptography. As you famous, that’s not as straightforward correctly. “Fairly often, you’re going to want to make use of subtle instruments which can be being developed to help with that. Additionally discuss to your distributors, your CIOs, your CEOs to ensure they’re conscious and that they’re planning for budgets to do that. Simply because a quantum laptop [able to decrypt] isn’t going to be constructed for, who is aware of, possibly 15 years, they could suppose I can simply put this off, however understanding that menace is coming prior to than you understand is necessary.”
HPCwire: Thanks on your time!
In accordance with the second and third targets above (Submission Necessities and Analysis Standards for the Put up-Quantum Cryptography Standardization Course of), NIST will base its classification on the vary of safety strengths provided by the prevailing NIST requirements in symmetric cryptography, which NIST expects to supply important resistance to quantum cryptanalysis. Specifically, NIST will outline a separate class for every of the next safety necessities (listed so as of accelerating strength2 ):
1) Any assault that breaks the related safety definition should require computational sources similar to or larger than these required for key search on a block cipher with a 128-bit key (e.g. AES-128)
2) Any assault that breaks the related safety definition should require computational sources similar to or larger than these required for collision search on a 256-bit hash operate (e.g. SHA-256/ SHA3-256)
3) Any assault that breaks the related safety definition should require computational sources similar to or larger than these required for key search on a block cipher with a 192-bit key (e.g. AES-192)
4) Any assault that breaks the related safety definition should require computational sources similar to or larger than these required for collision search on a 384-bit hash operate (e.g. SHA-384/ SHA3-384)
5) Any assault that breaks the related safety definition should require computational sources similar to or larger than these required for key search on a block cipher with a 256-bit key (e.g. AES-256)
Editor’s be aware: This text first ran in HPCwire.