
Chinese language risk actors are focusing on ThinkPHP purposes susceptible to CVE-2018-20062 and CVE-2019-9082 to put in a persistent net shell named Dama.
The online shell allows additional exploitation of the breached endpoints, equivalent to enlisting them as a part of the attackers’ infrastructure to evade detection in subsequent operations.
The primary indicators of this exercise date again to October 2023, however based on Akamai analysts monitoring it, the malicious exercise has just lately expanded and intensified.
Focusing on previous vulnerabilities
ThinkPHP is an open-source net software improvement framework that’s notably widespread in China.
CVE-2018-20062, mounted in December 2018, is a matter found in NoneCMS 1.3, permitting distant attackers to execute arbitrary PHP code through crafted use of the filter parameter.
CVE-2019-9082 impacts ThinkPHP 3.2.4 and older, utilized in Open Supply BMS 1.1.1., is a distant command execution drawback addressed in February 2019.
The 2 flaws are leveraged on this marketing campaign to allow the attackers to carry out distant code execution, impacting the underlying content material administration methods (CMS) on the goal endpoints.
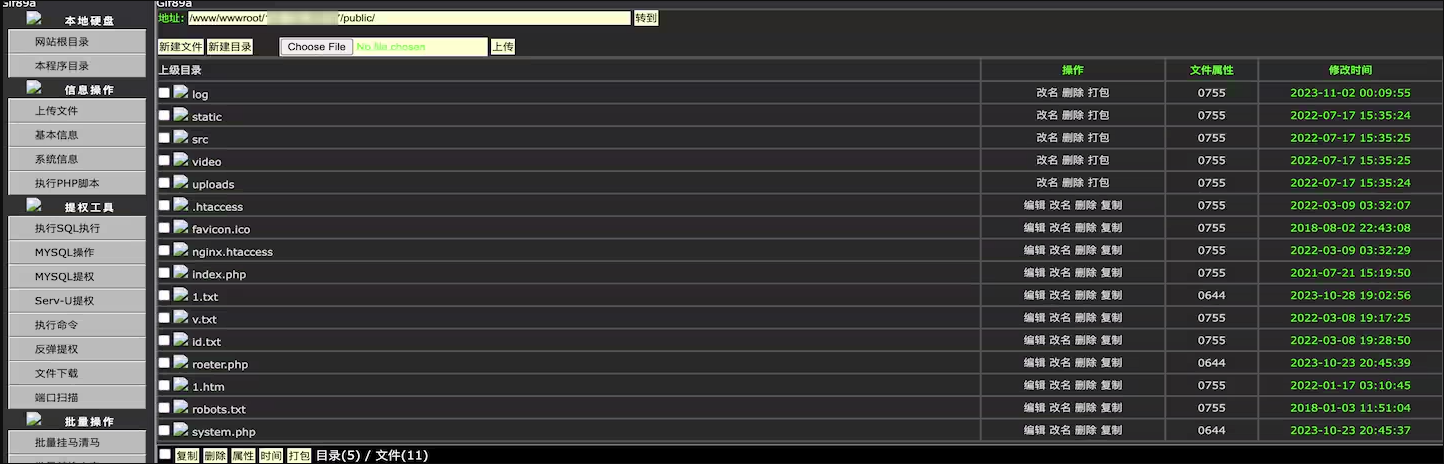
Particularly, the attackers exploit the bugs to obtain a textual content file named “public.txt,” which, in actuality, is the obfuscated Dama net shell saved as “roeter.php.”
The payload is downloaded from compromised servers situated in Hong Kong and supplies the attackers with distant server management following a easy authentication step utilizing the password “admin.”
Akamai says the servers delivering the payloads are contaminated themselves with the identical net shell, so it seems that compromised methods are become nodes within the attacker’s infrastructure.
The Dama net shell
Dama has superior capabilities enabling the risk actors to navigate the file system on the compromised server, add information, and collect system knowledge, basically aiding in privilege escalation.
It may additionally carry out community port scanning, entry databases, and bypass disabled PHP capabilities for shell command execution.
Supply: Akamai
A notable omission from Dama’s capabilities is the dearth of a command-line interface, which might enable risk actors a extra hands-on method to executing instructions.
Akamai notes that this lacking performance is notable given Dama’s in any other case intensive performance.
Mitigation
Exploiting 6-year-old flaws serves as one other reminder of the persistent drawback of poor vulnerability administration, as attackers, on this case, leverage safety vulnerabilities patched a very long time in the past.
The really useful motion for doubtlessly impacted organizations is to maneuver to the latest ThinkPHP, model 8.0, which is secure towards identified distant code execution bugs.
Akamai additionally notes that the focusing on scope of this marketing campaign is broad, even impacting methods not utilizing ThinkPHP, which suggests opportunistic motives.
