Russian organizations are on the receiving finish of cyber assaults which were discovered to ship a Home windows model of a malware referred to as Decoy Canine.
Cybersecurity firm Optimistic Applied sciences is monitoring the exercise cluster underneath the identify Operation Lahat, attributing it to a complicated persistent menace (APT) group referred to as HellHounds.
“The Hellhounds group compromises organizations they choose and achieve a foothold on their networks, remaining undetected for years,” safety researchers Aleksandr Grigorian and Stanislav Pyzhov stated. “In doing so, the group leverages major compromise vectors, from weak internet companies to trusted relationships.”
HellHounds was first documented by the agency in late November 2023 following the compromise of an unnamed energy firm with the Decoy Canine trojan. It is confirmed to have compromised 48 victims in Russia thus far, together with IT corporations, governments, house business companies, and telecom suppliers.
There may be proof indicating that the menace actor has been focusing on Russian corporations since at the very least 2021, with the event of the malware underway way back to November 2019.
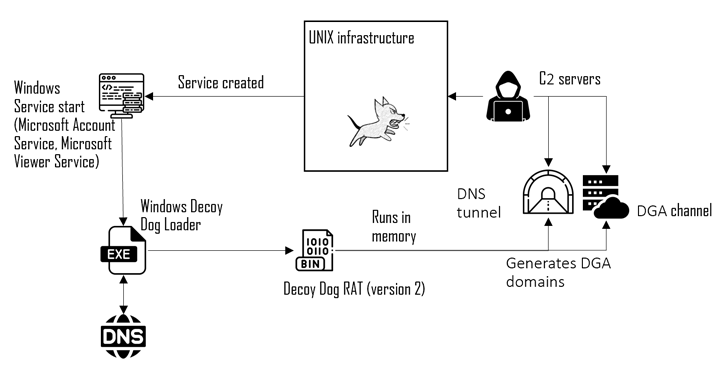
Particulars about Decoy Canine, a customized variant of the open-source Pupy RAT, emerged in April 2023, when Infoblox uncovered the malware’s use of DNS tunneling for communications with its command-and-control (C2) server to remotely management contaminated hosts.
A notable characteristic of the malware is its means to maneuver victims from one controller to a different, permitting the menace actors to keep up communication with compromised machines and stay hidden for prolonged durations of time.
Assaults involving the subtle toolkit have been primarily confined to Russia and Jap Europe, to not point out completely single out Linux methods, though Infoblox hinted at the potential of a Home windows model.
“References to Home windows within the code trace towards the existence of an up to date Home windows shopper that features the brand new Decoy Canine capabilities, though the entire present samples are focusing on Linux,” Infoblox famous again in July 2023.
The most recent findings from Optimistic Applied sciences all however verify the presence of an an identical model of Decoy Canine for Home windows, which is delivered to mission-critical hosts by way of a loader that employs devoted infrastructure to get the important thing for decrypting the payload.
Additional evaluation has uncovered HellHounds’ use of a modified model of one other open-source program referred to as 3snake to acquire credentials on hosts working Linux.
Optimistic Applied sciences stated that in at the very least two incidents, the adversary managed to achieve preliminary entry to victims’ infrastructure through a contractor utilizing compromised Safe Shell (SSH) login credentials.
“The attackers have lengthy been capable of keep their presence inside vital organizations situated in Russia,” the researchers stated.
“Though just about the entire Hellhounds toolkit is predicated on open-source tasks, the attackers have achieved a reasonably good job modifying it to bypass malware defenses and guarantee extended covert presence inside compromised organizations.”