How To
Password leaks are more and more frequent and determining whether or not the keys to your personal kingdom have been uncovered may be difficult – except you already know the place to look
03 Jun 2024
•
,
6 min. learn

Just lately, I got here throughout a report detailing “the mom of all breaches” – or to be extra precise, the leak of an enormous compilation of knowledge that was stolen throughout plenty of assaults on numerous firms and on-line companies, together with LinkedIn and Twitter (now X). The information cache reportedly comprised an astonishing 26 billion information that have been replete with a spread of delicate data, together with authorities knowledge and other people’s login credentials.
Whereas this isn’t the primary time {that a} huge stash of person knowledge has been there for the taking, the sheer variety of compromised information eclipsed earlier identified leaks (and their compilations). Simply think about that the notorious Cam4 knowledge leak in 2020 uncovered near 11 billion information of assorted sort and the breach at Yahoo in 2013 compromised all three billion person accounts. Lest we overlook: the aptly named Assortment No. 1, which made it onto the open web in 2019, uncovered 773 million login names and passwords beforehand stolen from numerous organizations, earlier than being adopted by 4 extra “collections” of this type simply weeks later.
The place does that depart us? Maybe the important thing takeaway is that even should you apply stringent private safety measures, your account credentials can nonetheless get caught up in such collections, primarily as a consequence of breaches at giant firms. This begs the query – how are you going to discover out in case your credentials have been compromised? Learn on.
Firm disclosures
Enterprise could also be topic to particular regulatory necessities that oblige them to reveal hacking incidents and unpatched vulnerabilities. Within the U.S., as an example, publicly-traded firms have to report “materials” cyber-incidents to the U.S. Securities and Trade Fee (SEC) inside 96 hours, or 4 enterprise days, of their incidence.
How does this assist common folks? Such transparency could not solely assist construct belief with prospects however it additionally informs them if their accounts or knowledge have been compromised. Corporations usually notify customers of knowledge breaches by way of e mail, however since SEC filings are public, it’s possible you’ll study such incidents from different sources, probably even information reviews overlaying them.
Have I been pwned?
Maybe the best means of checking whether or not a few of your knowledge, resembling your e mail tackle or any of your passwords, has been uncovered in a knowledge leak is to go to haveibeenpwned.com. The positioning includes a free device that may inform you when and the place your knowledge popped up.
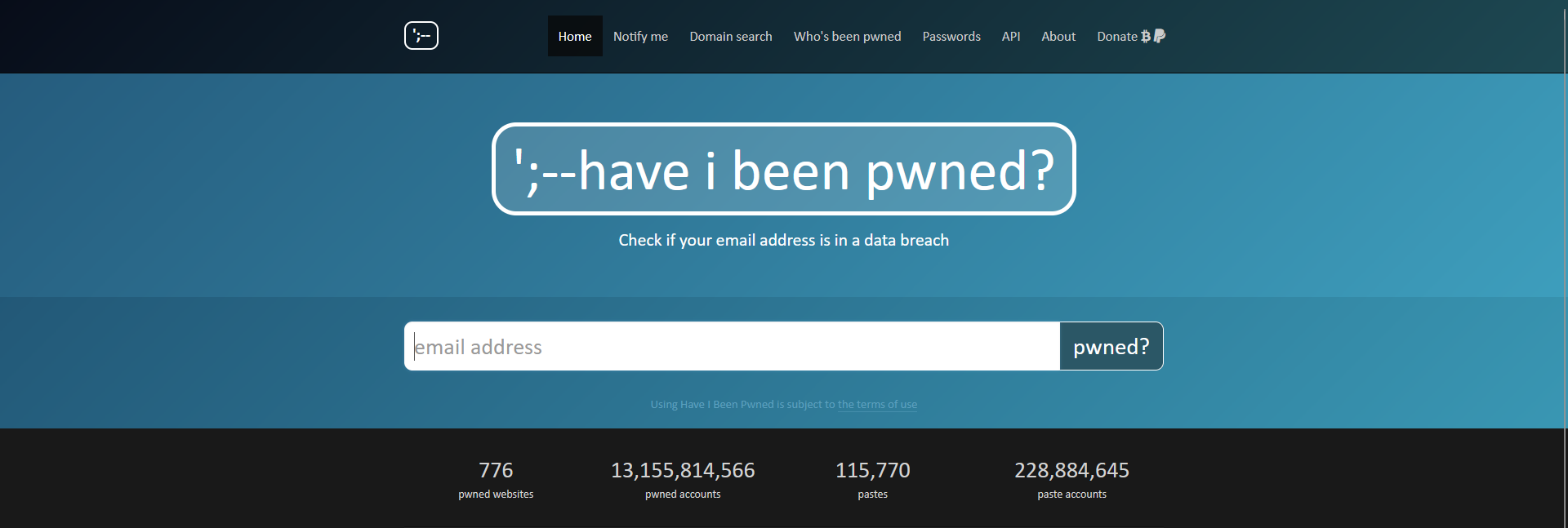
Merely enter your e mail tackle, click on “pwned?” and voila! A message will seem informing you of the safety standing of your credentials in addition to the precise leak they have been caught up in. For many who are fortunate, the consequence can be inexperienced, signaling no pwnage, and for these much less lucky, the positioning will flip purple, itemizing during which knowledge leak(s) your credentials appeared.
Net browsers
Some net browsers, together with Google Chrome and Firefox, can test in case your passwords have been included in any identified knowledge leak. Chrome may suggest stronger passwords by way of its password supervisor module or provide different options to reinforce your password safety.
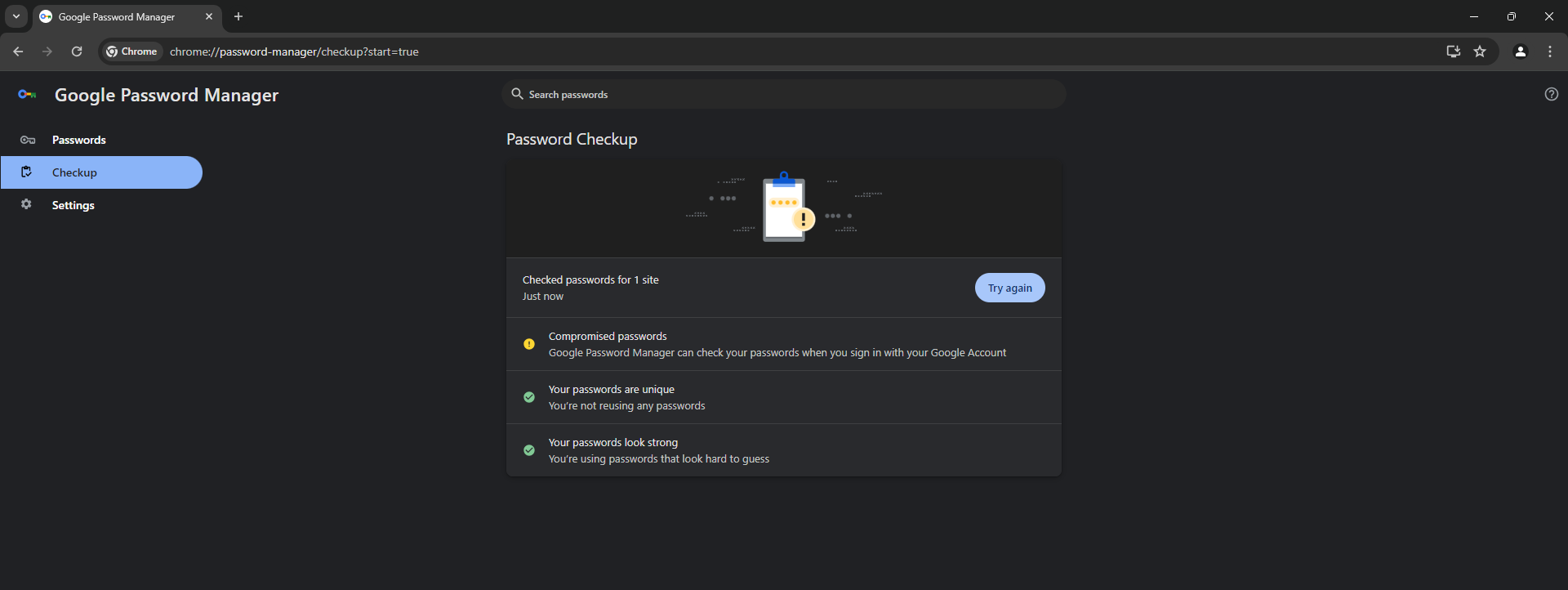
Nevertheless, it’s possible you’ll wish to up your recreation additional and use a devoted password supervisor that has a confirmed monitor document of taking knowledge safety severely, together with by way of strong encryption. These instruments are additionally typically bundled with respected multi-layered safety software program.
Password managers
Password managers are invaluable in relation to juggling a big assortment of login credentials, as they cannot solely securely retailer them, however generate complicated and distinctive passwords for every of your on-line accounts. It ought to go with out saying, nevertheless, that it’s worthwhile to use a powerful however memorable grasp password that holds the keys to your kingdom.
However, these password vaults aren’t resistant to compromise and stay enticing targets for malicious actors, for instance because of credential-stuffing assaults or assaults exploiting software program vulnerabilities. Even so, the advantages – which embrace built-in leaked password checks and integration with two-factor authentication (2FA) schemes which might be accessible on many on-line platforms lately – outweigh the dangers.
The right way to stop (the affect of) credential leaks?
Now, what about stopping leaks within the first place? Can a mean web person defend themselves in opposition to credential leaks? In that case, how? Certainly, how are you going to maintain your accounts secure?
To begin with, and we will’t stress this sufficient, don’t depend on passwords alone. As an alternative, ensure that your accounts are protected by two types of identification. To that finish, use two-factor authentication (2FA) on each service that permits it, ideally within the type of a devoted safety key for 2FA or an authenticator app resembling Microsoft Authenticator or Google Authenticator. This can make it considerably more durable for attackers to achieve unauthorized entry to your accounts – even when they’ve in some way acquired their arms in your password(s).
Associated studying: Microsoft: 99.9 p.c of hacked accounts didn’t use MFA
As for password safety as such, keep away from writing your logins down on paper or storing them in a note-taking app. It’s additionally higher to keep away from storing your account credentials in net browsers, which normally solely retailer them as easy textual content information, making them weak to knowledge exfiltration by malware.
Different fundamental account safety suggestions contain utilizing sturdy passwords, which make it more durable for crooks to commit brute-force assaults. Steer clear of easy and quick passwords, resembling a phrase and a quantity. When doubtful, use this ESET device to generate your passwords, or have it test the energy of your personal passwords.
Associated studying: How typically do you have to change your passwords?
It’s additionally good observe to use passphrases, which could be safer in addition to simpler to recollect. As an alternative of random letter and image mixtures, they comprise a sequence of phrases which might be sprinkled by capitals and probably particular characters.
Likewise, use a distinct password for every of your accounts to stop assaults resembling credential stuffing, which takes benefit of individuals’s penchant for reusing the identical credentials throughout a number of on-line companies.
A more moderen strategy to authentication depends on passwordless logins, resembling passkeys, and there are additionally different login strategies like safety tokens, one-time codes or biometrics to confirm account possession throughout a number of gadgets and methods.
Firm-side prevention
Corporations have to spend money on safety options, resembling detection and response software program, that may stop breaches and safety incidents. Moreover, organizations have to proactively shrink their assault floor and react as quickly as one thing suspicious is detected. Vulnerability administration can be essential, as staying on high of identified software program loopholes and patching them in a well timed method helps stop exploitation by cybercriminals.
In the meantime, the ever-present human issue may set off a compromise, for instance after an worker opens a suspicious e mail attachment or clicks a hyperlink. This is the reason the significance of cybersecurity consciousness coaching and endpoint/mail safety can’t be understated.
Associated studying: Strengthening the weakest hyperlink: high 3 safety consciousness subjects on your staff
Any firm that severely tackles knowledge safety must also think about a knowledge loss prevention (DLP) answer and implement a strong backup coverage.
Moreover, dealing with giant volumes of shopper and worker knowledge requires stringent encryption practices. Native encryption of credentials can safeguard such delicate knowledge, making it tough for attackers to take advantage of stolen data with out entry to the corresponding encryption keys.
All in all, there isn’t a one-size-fits-all answer, and each firm must tailor its knowledge safety technique to its particular wants and adapt to the evolving menace panorama. However, a mixture of cybersecurity greatest practices will go a good distance in direction of stopping knowledge breaches and leaks.


